Using X.509 Certs for DID Provenance
Phil Windley
APRIL 25, 2024
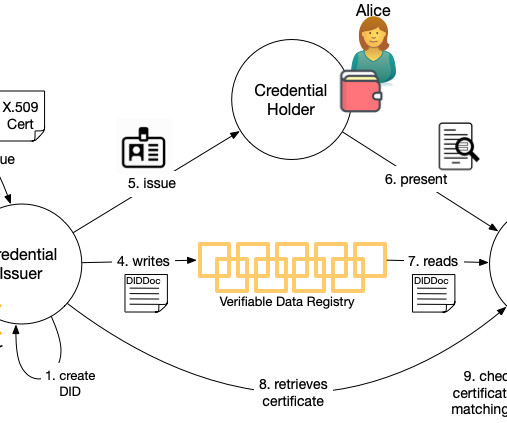
At the most recent Internet Identity Workshop , Drummond Reed gave a session on how X.509 509 certificate providing TLS security. Provided the certificate includes information about the entity beyond the domain name, the verifier can use that information to determine whether or not the credential is authentic (i.e.,














Let's personalize your content