Alexa, is this a scam? Amazon alleges tech support sites used fake apps to trick new users into paying to fix bogus bugs
GeekWire
MAY 14, 2020
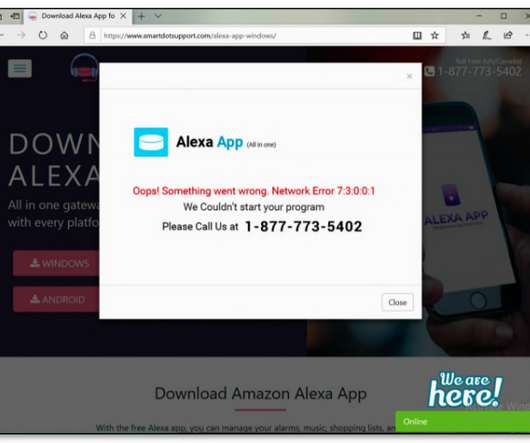
Amazon is suing two companies for “widespread tech support fraud,” alleging that they tricked new users of Echo speakers and other Alexa devices into paying for purported technical support through an elaborate ruse designed to convince them they had encountered frustrating technical glitches. ” A purported network firewall.




















Let's personalize your content