Is voice being superseded?
Spearline Testing
MAY 10, 2021
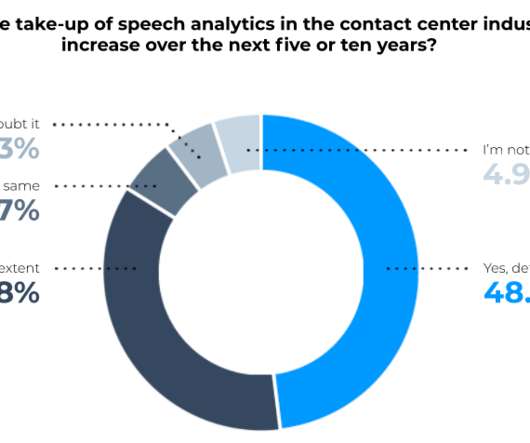
* This article is an excerpt taken from Spearline's Whitepaper ' 2020 Global Telecom's Report ' Businesses continue expanding their contact channels, and inbound voice is sometimes seen as outdated in this omnichannel world. Yet the inbound voice is far from obsolete.













Let's personalize your content