How Cloud-Based OS and Device Management Help SMBs Modernize and Secure Workforce Tech
IT Toolbox
SEPTEMBER 21, 2023
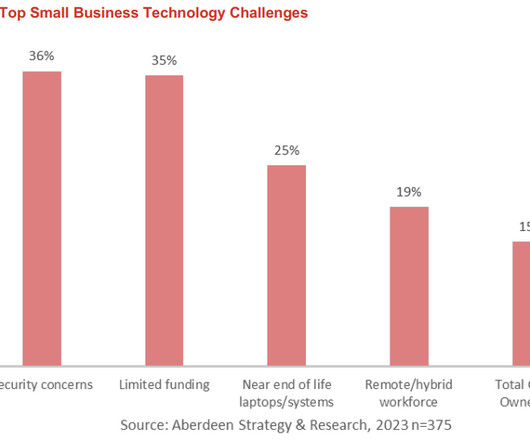
The post How Cloud-Based OS and Device Management Help SMBs Modernize and Secure Workforce Tech appeared first on Spiceworks. Over a third of small businesses have not upgraded their systems for four or more years.


















































Let's personalize your content