Nokia, Telenor invest to address new enterprise security threats
TM Forum
MAY 25, 2022
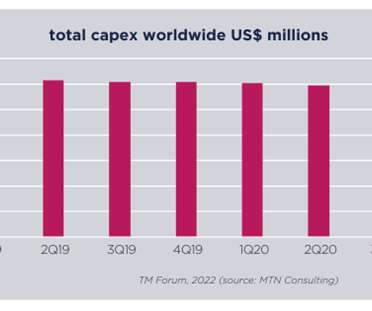
As 5G and B2B services for vertical industries start to take deeper root, Nokia and Telenor are among the companies launching new initiatives to protect enterprise systems from emerging security threats. a new security software joint venture. Nokia’s initiative is. ” Telenor meanwhile has announced.




















Let's personalize your content