How to Create AppLocker Policies to Secure Windows Environments Intune
Anoop
MARCH 18, 2020
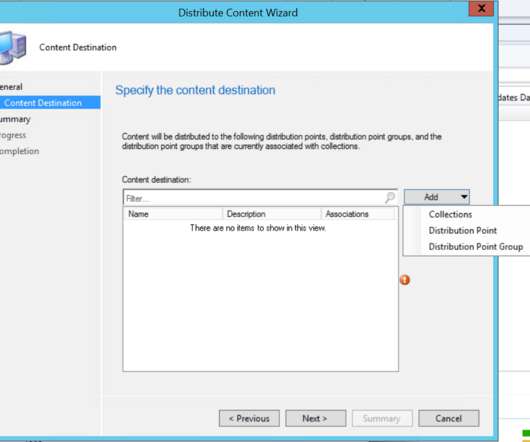
Let’s check how to create AppLocker Policies to Secure Windows Environments. Introduction Applocker is introduced with the Windows 7 operating system, Windows Server 2008 R2. The post How to Create AppLocker Policies to Secure Windows Environments Intune appeared first on SCCM|Intune|WVD|Azure| Windows by Jitesh Kumar.












































Let's personalize your content