Free your business to accelerate into change
CIO Business Intelligence
MARCH 26, 2024
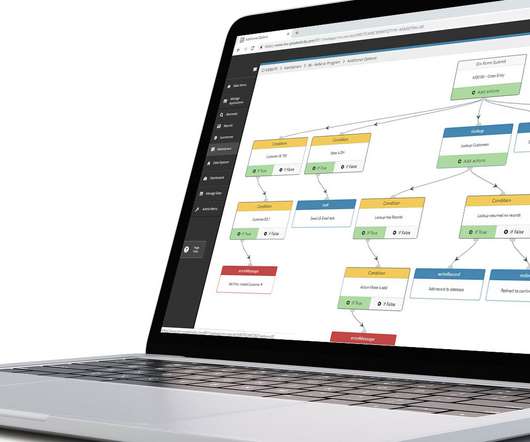
To help meet sustainability goals, migrating print solutions from on-premise data centers to the HP cloud can help keep your carbon footprint down. Empower people to work in the way that best suits their needs, with authentication, job accounting, and pull-print solutions. Click here to read the full guide.































Let's personalize your content