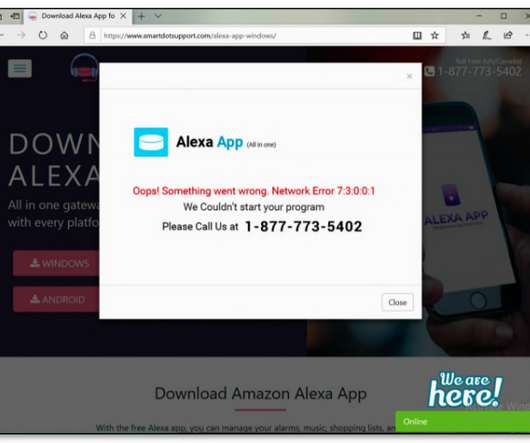
Alexa, is this a scam? Amazon alleges tech support sites used fake apps to trick new users into paying to fix bogus bugs
GeekWire
MAY 14, 2020
. “Among other things, this extension falsely purports to provide a firewall. In the firewall section of the extension, an animation shows that the firewall is off. The animation then shows a loading power button that turns green and then states the firewall is on. The extension does not create a firewall.”

























Let's personalize your content