10 essential Linux tools for network and security pros
Network World
APRIL 7, 2022
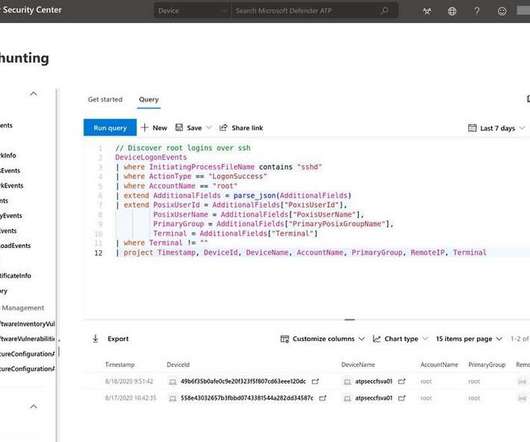
Picking just 10 Linux open source security tools isn’t easy, especially when network professionals and security experts have dozens if not several hundred tools available to them. There are different sets of tools for just about every task—network tunneling, sniffing, scanning, mapping.











































Let's personalize your content