Anatomy of an Effective Tabletop Exercise
Information Week
JULY 16, 2024
Tabletops can boost cyber resilience, but what does it take to execute an effective exercise?
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
 Exercises Related Topics
Exercises Related Topics 
Information Week
JULY 16, 2024
Tabletops can boost cyber resilience, but what does it take to execute an effective exercise?

Association of Information Technology Professional
SEPTEMBER 6, 2022
Find out more about how tabletop exercises can help your organization better prepare for a multitude of risk scenarios and threats. There are many benefits to regularly testing your incident response plan.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Forrester IT
JULY 8, 2022
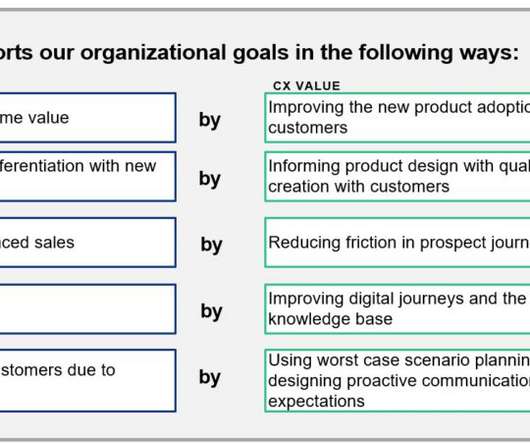
How can CX leaders gain funding? Develop executive empathy: Determine stakeholder priorities, connect CX to these existing priorities, and communicate the value of CX.

SecureWorld News
DECEMBER 6, 2022
NATO's largest annual cyber defense exercise took place Nov. The exercise was led by NATO's Allied Command Transformation. More than 1,000 cybersecurity professionals took part in Cyber Coalition 2022 with the goal of testing and training cyber defenders in their ability to defend NATO and national networks. 28 to Dec.

CTOvision
AUGUST 13, 2020
According to research by Immersive Labs of 402 organizations, nearly 40% are not fully confident in their teams training to handle a data breach if one occurred, and 65% of […].

Forrester IT
MARCH 30, 2020
Value for customer is a customer’s perception of what they get versus what they give up when doing business with a firm. Four dimensions make up the overall value a customer perceives: 1) functional, 2) experiential, 3) symbolic, and 4) economic. But which combination is the right one? Find Your Organization’s Value Sweet Spot!

Venture Beast
SEPTEMBER 27, 2021
Playpulse has raised $2 million to build the Playpulse One, an exercise bike that motivates people to work out using games. Read More.

Gizmodo
JANUARY 11, 2022
New research adds to evidence that exercise can improve cognition, especially later in life. The study found that older people who regularly exercised had greater levels of proteins crucial to their brain’s health, compared to those who didn’t exercise. These differences were apparent even in people whose brains… Read more.

Forrester IT
AUGUST 14, 2018
Journey mapping can be an energizing and eye-opening exercise in customer empathy. As advisors to B2B CX and Marketing Leaders in the Forrester Leadership Boards (FLB), we come along on many journey mapping “journeys”.

Gizmodo
NOVEMBER 2, 2021
For those interested in exercising more but worried about their knees, a new study from researchers in the UK this week might offer some reassurance. The research, a review of existing evidence, found no link between exercise and a greater risk of knee osteoarthritis, the most common form of arthritis to plague the… Read more.

Forrester IT
JUNE 18, 2020
Infections are in the rise in more than 20 US states, and at least a dozen have experienced new record rates of infections. And the US isn’t alone; China and Brazil are experiencing a rise, too. Officials say the chance of a second wave is high. Over the last few months, we’ve been providing advice […].

The Verge
APRIL 14, 2022
However, new, lower prices for Peloton’s exercise equipment are set to go into effect at 6PM ET today, according to CNBC — the Bike will cost $1,445 (including a $250 shipping fee) instead of $1,745, the Bike Plus will go for $1,995 instead of $2,495, while the Tread will drop to $2,695 (including a $350 shipping fee) from $2,845.

The Verge
FEBRUARY 22, 2022
But in the meantime, you might have to just exercise without a leaderboard. That said, as Peloton’s new CEO, Barry McCarthy, emphasized over the weekend , content and the on-screen experience are the company’s bread and butter. Of course, Peloton will eventually be back online. We are currently investigating an issue with Peloton services.

The Verge
JUNE 29, 2020
The fitness lifestyle company announced on Monday it would spend $500 million to acquire the startup, which sells a $1,495 reflective display so subscribers can exercise while simultaneously streaming workouts and watching themselves. Lululemon, the company behind trendy fitness apparel, is getting into the hardware business with Mirror.

Forrester IT
MARCH 18, 2020
A recent debate on Twitter surrounding the ethics of organizations using COVID-19 as a theme for phishing exercises sparked our interest, since it relates to our coverages areas and prior work experience. In one of Brian’s prior jobs, he conducted the phishing exercises for the employees of one of the larger security companies.

Forrester IT
OCTOBER 4, 2022
I believed that competency mapping was a theoretical exercise invented by human resources or learning designers to test my last nerve. I was certain that the exercise would […]. When I was a first-time sales enablement practitioner, just the mention of “competencies” made my eyes glaze over and my attention immediately wane.

Forrester IT
NOVEMBER 2, 2020
Sales enablement practitioners must deconstruct role-playing exercises to enable reps to get into top-selling form. Like in golf, there are so many motions to consider in any customer interaction.

Information Week
MAY 3, 2024
At what point does continuous, iterative development for Agile applications turn into a maintenance exercise?
Forrester IT
JULY 20, 2022
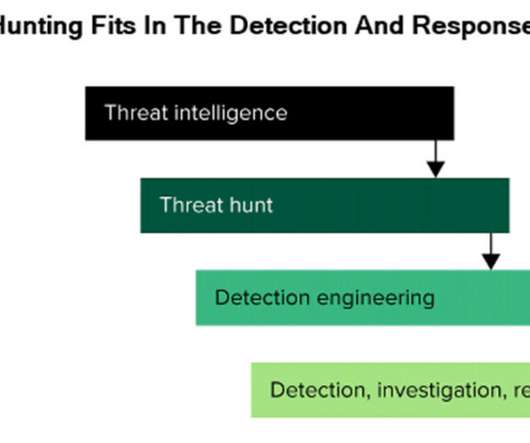
Threat hunting is a term frequently misused by cybersecurity pros, vendors, and service providers. We researched threat hunting to determine what it really is, what benefits it brings, and to overcome the misuse and abuse of the term. The resulting report, Threat Hunting 101, published recently.

TechSpot
MARCH 6, 2023
When the first Amazon Go store opened in Seattle in 2018 following a lengthy delay, its Just Walk Out technology that allows shoppers to pick items off the shelves and leave was hailed as the future of shopping: no lines, checkouts, or registers, with the bill automatically charged to a. Read Entire Article
GeekWire
JUNE 3, 2021
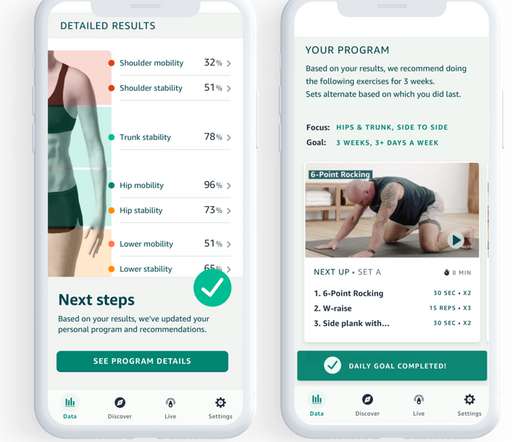
Amazon is adding a new feature to its Halo health app, using computer vision and machine learning to score users’ stability, posture and mobility in four different areas of the body, and offering a series of exercises designed to improve their ability to make routine movements based on the results.

Network World
OCTOBER 14, 2016
The Royal Navy is testing just how much robot craft can do by themselves in military exercises off the British coast. Operation Unmanned Warrior 16 is a chance for allied nations and the defense industry to show off their latest maritime autonomous systems, as part of a broader military exercise called Joint Warrior.

Forrester IT
JULY 22, 2019
The Value Of Brand Valuing a brand can be a deeply divisive exercise. Questioning it, or attempting to validate it, can well be an exercise in futility and mathematical mumbo jumbo. To most marketers, there is an axiomatic simplicity to brand value.

IT Toolbox
OCTOBER 12, 2022
Cybersecurity is not just a tick-in-the-box exercise, nor simply a product to sell. The post Moving Cybersecurity Forward: Takeaways from International Cyber Expo 2022 appeared first on Spiceworks.

IT Toolbox
OCTOBER 19, 2022
In July, Microsoft indicated that it could lay off less than 1% of its workforce as part of a structural adjustment exercise. The post Microsoft Lets Go of 1,000 Employees In Latest Round of “Structural Adjustments” appeared first on Spiceworks.

Forrester IT
AUGUST 3, 2021
Needless to say the exercise is becoming more and more difficult and anything beyond 24 to 60 months looks very futuristic. As analysts, part of our jobs is to try to decipher the broader trends impacting businesses. That’s why I enjoy reading prospective books and especially publications of the National Intelligence Council.

Forrester IT
JULY 12, 2021
Once you’ve got Kubernetes in production, those predictable business continuity and disaster recovery (DR) exercises get a lot more interesting — and not necessarily in a good way. That’s why I’m focusing on the challenges of Kubernetes disaster recovery and business continuity in my recently published research.

Venture Beast
APRIL 13, 2021
Balan Wonderworld is a bad game, and you should not pay $10 for it let alone $60. Although it is fun as a bad game to broadcast on Twitch. Read More.

Forrester IT
MARCH 1, 2021
This is an exercise we do every year to hold us — the prediction-makers — accountable to our predictions. This week, we published scores for our 2020 cloud predictions. We assess if our predictions came to pass and explicitly call out if we were vague, too aggressive, or just simply wrong. Although we pride ourselves […].

Association of Information Technology Professional
NOVEMBER 23, 2020
Developing an incident response plan and running a war gaming exercise gives employees the tools they need to respond quickly, mitigate the situation and return to business as usual. Everyone should be prepared for a cyberattack.

Tech Republic Security
FEBRUARY 26, 2020
In a RSA 2020 simulation, the Red Team compromised email accounts, created deepfake videos and spread disinformation on Election Day in Adversaria.
GeekWire
DECEMBER 31, 2020
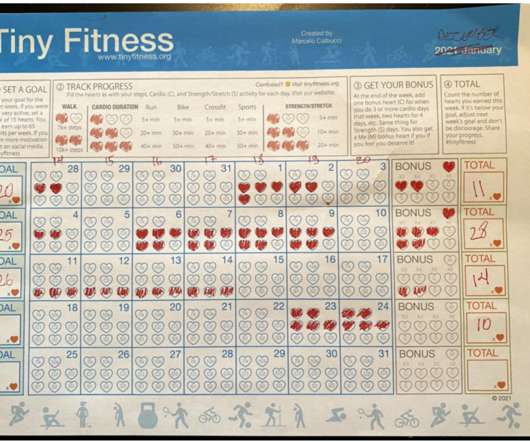
A beta version of the Tiny Fitness sheet we used. The kids (D & V) won that week. Photo courtesy of Marcelo Calbucci). It’s not integrated with Apple Fitness or Peloton. It has no companion app or website. It won’t send you reminder emails or notifications. That’s the fitness tracking/challenge I put together for my family.

Computer Weekly
JUNE 29, 2017
How should organisations address the need to keep software up to date with security patches without it costing too much or being too labour intensive?

Gizmodo
SEPTEMBER 23, 2020
Just yesterday it seemed like a Peloton challenger had arrived. Echelon Fitness casually dropped the news it was launching the “Ex-Prime Smart Connect Bike,” or a $500 stationary bike that it claimed was “Amazon’s first-ever connected fitness product.” Except now Amazon is crying foul, saying it has nothing to do with… Read more.

Forrester IT
MAY 16, 2019
Rather than undertake a full organizational design exercise, firms are adopting tactical change, creating agile delivery […]. Many firms have used Forrester’s principles of customer obsession to guide their business and IT transformation journey, striving to be customer-led, insights-driven, fast, and connected.

Forrester IT
JANUARY 31, 2020
When starting a project like the Future of the CISO – it’s a daunting exercise. While we don’t always share the background inspiration for our research, this time it’s quite important and will shed some light on how we arrived here. When we started planning this research in 2018 and working on it in 2019, […].

TechSpot
MARCH 15, 2024
The program is a mix of "physical and mental activities, wellness exercises, and healthy eating support" that supposedly helps overworked employees recharge and reenergize. Amazon announced it was introducing ZenBooths in 2021 as part of the company's wellness and meditation regime called "Working Well," or, unironically, "AmaZen."

Future of CIO
APRIL 16, 2018
A “powerful” board can exercise supervisory power and co-determine of which powers are retained by the governing body and which are delegated to management, along with constraints that may apply. The “sovereign” power: Generally, the shareholders of the company exercise this third power.

Gizmodo
MAY 14, 2021
My cat Pablo is fat. His fluffy tummy flops wildly from side to side when he runs, and he only runs to his food bowl. On the chart of chonky cats , he is most definitely a “megachonker” and a kibble binge or two away from graduating to “oh lawd he comin’.” I wake up most mornings to his tail smacking my face as he… Read more.

Forrester IT
JANUARY 15, 2019
Every New Year, I find myself making lofty goals: eat better, exercise more, spend less time on social media. By mid-February, those goals are a distant blip in my rearview mirror; the reality of life gets into the way and I just fail at tracking progress. But this year is different (I swear). I created […]

TechSpot
JULY 19, 2022
Apple could face a new antitrust lawsuit in the coming months. Bloomberg notes that Affinity Credit Union (ACU), out of Iowa, has hired representation to contest Apple's tap-to-pay system. Its lawyers are looking into whether they can create a class-action case of the complaint.

Gizmodo
OCTOBER 25, 2020
A sale on Ativafit exercise equipment and I Dew Care facial mask sets lead Sunday’s best deals. Read more.

TechSpot
DECEMBER 12, 2023
Trying to stream your favorite movie or play that critical match in Fortnite can be an exercise is futility if there's a lot of latency (or lag) disrupting the experience. For most people with decent Internet connection speeds, latency isn't usually that big of an issue. until it is. Read Entire Article

TechSpot
OCTOBER 20, 2023
As reported by The Warzone, members of the Marine Air Ground Task Force Training Command's (MAGTFC) Tactical Training and Exercise Control group (TTECG), based at the Marine Corps Air Ground Combat Center at Twentynine Palms in California, tested the robot dog in September. Read Entire Article
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content