Microsoft Pluton is a new processor with Xbox-like security for Windows PCs
The Verge
NOVEMBER 17, 2020
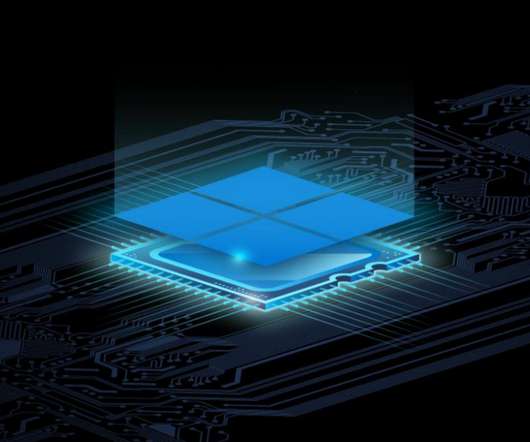
Microsoft is creating a new security chip that’s designed to protect future Windows PCs. Microsoft Pluton is a security processor that is built directly into future CPUs and will replace the existing Trusted Platform Module (TPM), a chip that’s currently used to secure hardware and cryptographic keys. so you just get it.”



























Let's personalize your content