Customers Are Staying Home — So Prioritize Digital UX
Forrester IT
MARCH 27, 2020
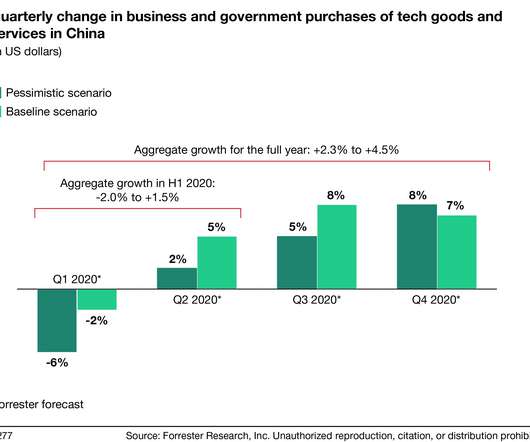
Your customers are stuck at home so it’s suddenly more important than ever to get digital experiences right. Redirect funds to 1) scale up your design team, 2) hire outside help where needed, 3) rigorously review your UX so you can make it better, and 4) update and sharpen your UX expertise. Forrester's research reports and advisory services can help with all four.


























Let's personalize your content