No, the Cloud Is Not a Green Technology
Information Week
FEBRUARY 28, 2022
Since the cloud is nothing more than a rented data center that someone else owns, cloud computing itself can't be much greener than any other data center technology.

Information Week
FEBRUARY 28, 2022
Since the cloud is nothing more than a rented data center that someone else owns, cloud computing itself can't be much greener than any other data center technology.

Association of Information Technology Professional
FEBRUARY 9, 2022
Being on the forefront of technology now includes effective policies around data management and analytics.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Anoop
FEBRUARY 23, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SCCM CMPivot query to check Windows 11 Compatibility appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Security
FEBRUARY 18, 2022
Corporate users are more aware of phishing attacks in their mailboxes. Yet they are not used to being targeted via other systems like Microsoft Teams. Learn how to protect yourself. The post Cyberattack threat: Corporate users infected via Microsoft Teams appeared first on TechRepublic.

Advertisement
With its unparalleled flexibility, rapid development and cost-saving capabilities, open source is proving time and again that it’s the leader in data management. But as the growth in open source adoption increases, so does the complexity of your data infrastructure. In this Analyst Brief developed with IDC, discover how and why the best solution to this complexity is a managed service, including: Streamlined compliance with some of the most complex regulatory guidelines Simplified operations, li

Tech Republic Cloud
FEBRUARY 24, 2022
To spot faults quickly even if they take a month to show up, Azure feeds signals into a machine learning system: in the future, you will be able to do that for your own cloud workloads. The post Machine learning: The AIOps system Azure uses to make the cloud reliable appeared first on TechRepublic.

Network World
FEBRUARY 25, 2022
2022 will be another busy year for enterprise incident responders as ransomware, supply chain and myriad zero-day attacks will continue to rise, according to Cisco's Talos security experts. To help address the threats, the Cisco Talos team used a blog and online presentation to detail steps enterprises can take to defend themselves against the growing field of bad actors and also to point out lessons learned from recent damaging exploits such as the Log4j vulnerability and Microsoft Exchange ser
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

GeekWire
FEBRUARY 28, 2022
Microsoft CEO Satya Nadella and his wife Anu Nadella, photographed with their son, Zain. (Photo courtesy Microsoft and Seattle Children’s). Zain Nadella, the son of Microsoft CEO Satya Nadella and his wife, Anu Nadella, died Monday at the age of 26, according to a message sent to the company’s executives. “Zain will be remembered for his eclectic taste in music, his bright sunny smile and the immense joy he brought to his family and all those who loved him,” wrote Jeff Sp

Anoop
FEBRUARY 16, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows 365 Cloud PC Azure AD Joined Provisioning Process appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Security
FEBRUARY 11, 2022
The federal agency says hundreds of victims have lost money due to scams over a two-year span. The post FBI: Criminals escalating SIM swap attacks to steal millions of dollars appeared first on TechRepublic.
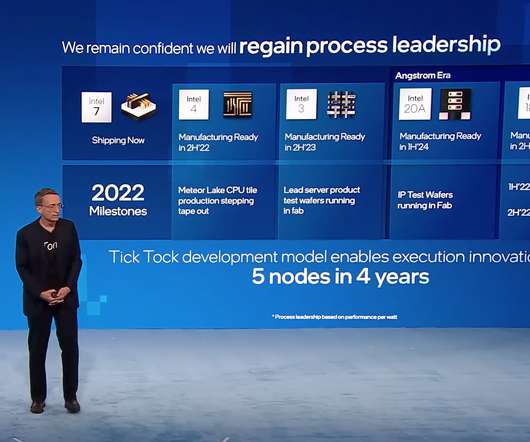
TechSpot
FEBRUARY 19, 2022
According to the milestones presented in the meeting, the first of the Intel 7 process node-based product line, known as Sapphire Rapids, is poised to hit the market in the first quarter of 2022.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.

The Verge
FEBRUARY 26, 2022
Illustration by Alex Castro / The Verge. As the invasion of Ukraine enters its third day, Russia has blocked access to Twitter in an apparent effort to stifle the flow of information, according to a report from the internet monitoring group NetBlocks. Beginning Saturday morning, NetBlocks saw failed or heavily throttled connections across every major Russian telecom provider, including Rostelecom, MTS, Beeline, and MegaFon.

Information Week
FEBRUARY 11, 2022
Automation is helping accelerate business processes and organizations. For those looking to land a job in IT automation, a long list of IT skills can be applied.

GeekWire
FEBRUARY 25, 2022
Rally in support of Ukraine at the University of Washington Thursday. (GeekWire Photo | Charlotte Schubert). As disinformation and Russian propaganda flood social media during the invasion of Ukraine, information experts are providing advice about how avoid propagating false narratives. Kate Starbird , director of the University of Washington’s Center for an Informed Public (CIP), shared her views in a series of tweets Thursday.

Anoop
FEBRUARY 18, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Configure Enterprise Mode Site List to Use IE Mode Using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.

Tech Republic Security
FEBRUARY 22, 2022
2021 saw a decrease in mobile malware attacks, yet they have become increasingly sophisticated. Learn more about these threats and how to avoid being a victim. The post 2021 mobile malware evolution: Fewer attacks, escalating dangers appeared first on TechRepublic.

Gizmodo
FEBRUARY 24, 2022
IDW’s Teenage Mutant Ninja Turtles comic series has taken the titular heroes and their half-shells on some wild adventures, playing with established TMNT canon in some fascinating ways. Now, their current story is going to include a major shock to the system: the return of a controversial, major figure from the team’s… Read more.
TechSpot
FEBRUARY 9, 2022
Intel says it has discovered no less than 16 new BIOS/UEFI vulnerabilities that allow malicious actors to perform escalation of privilege and denial of service attacks on affected systems. That means they can be leveraged to bypass many operating system protections as well as traditional endpoint security solutions, allowing hackers.

Information Week
FEBRUARY 4, 2022
Amid massive supply chain disruptions, companies are increasingly prioritizing sustainability and circularity to eliminate ‘take, make, waste’ and support better agility.

Advertiser: Procom Services
From streamlining the job search process to efficiently navigating the influx of applications, AI-powered tools can revolutionize your recruitment efforts. By combining the efficiency of AI with the expertise of experienced recruiters, you can identify the ideal candidates who not only possess the necessary skills but also align with your company culture.

GeekWire
FEBRUARY 11, 2022
Amy Sterner Nelson. Amy Sterner Nelson and Carleton Nelson have reached a settlement agreement with the U.S. government that will return most of their personal funds seized by the FBI as part of an investigation into Carleton Nelson’s activities in his past role as an Amazon real estate transaction manager. In a joint motion filed in federal court in Virginia , the Nelsons agreed to forfeit almost $109,000, while the government agreed to return the remaining $525,000 in seized funds.

Anoop
FEBRUARY 14, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post How to Install SCCM Client using Intune for Autopilot Provisioned Devices appeared first on HTMD Blog #1 by Kannan CS.

Tech Republic Security
FEBRUARY 24, 2022
Whether the chicken or the egg came first, Beyond Identity’s data suggests that the fastest growing companies are all more likely to take cybersecurity seriously. The post What hyper-growth companies all have in common: They prioritize cybersecurity appeared first on TechRepublic.

Gizmodo
FEBRUARY 11, 2022
The long saga of the union—and separation —of Marvel and Netflix’s shared superhero streaming ambitions is reaching a peculiar end , it seems. Quietly, Netflix has revealed that all six of its original Marvel streaming series will join a rare handful of Netflix Originals to leave the service, and it’s not sure yet if,… Read more.

Speaker: Kat Conner
The challenge of delivering the right product at the right time while aligning with strategic objectives is more pressing than ever. Product management is evolving and gaining greater recognition as the means to creating this connection. Join our upcoming webinar and learn how to streamline your product development processes, infuse product thinking across the organization, and bridge the gap between vision and delivery.

TechSpot
FEBRUARY 3, 2022
Microsoft CEO Satya Nadella recently held an interview with Financial Times (reprinted by Ars Technica), wherein he laid out the potential for the metaverse and its similarities with games. He went so far as to say the two are essentially the same thing.

Information Week
FEBRUARY 22, 2022
The answer for IT and business leaders facing exodus: Focus on product-led growth to limit the impact of talent departure and team productivity.

The Verge
FEBRUARY 23, 2022
Illustration by Alex Castro. Twitter says the accounts were removed in error As Russian troops and armored vehicles begin moving into Ukrainian territory , social media accounts sharing images and videos from the eastern Donbas and Luhansk regions have been a crucial source of information, sharing footage of Russian helicopters heading toward Crimea or tank divisions moving to the border.
Anoop
FEBRUARY 21, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SCCM Collection based on Active Directory OU | The Easy Way appeared first on HTMD Blog #1 by Anoop C Nair.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr

Tech Republic Security
FEBRUARY 25, 2022
The conflict we all feared is expected to bring an increase of cyberattacks, but experts agree that all hope isn’t lost. The post How Russia’s invasion of Ukraine will affect your cybersecurity appeared first on TechRepublic.

Gizmodo
FEBRUARY 8, 2022
Science fiction cinema would not be what it is today without the work of Douglas Trumbull. Trumbull helped drive effects on films like 2 001: A Space Odyssey , Blade Runner , and Close Encounters of the Third Kind , each time changing the field in ways that would resonate for decades. After an incredible life and career,… Read more.

TechSpot
FEBRUARY 23, 2022
ICQ, short for the phrase "I Seek You," laid the groundwork for standalone instant messaging clients when it arrived in November 1996. Think about how long ago that was. Windows 95 was barely a year old, Nintendo had just introduced the N64, and those with a reason to have a.

Information Week
FEBRUARY 14, 2022
A quantum pioneer reflects on his quantum startup days in the 2000s and discusses how the power of quantum is being applied today and where it has yet to go.

Advertisement
It’s no surprise that Apache Cassandra has emerged as a popular choice for organizations of all sizes seeking a powerful solution to manage their data at a scale—but with great power comes great responsibility. Due to the inherent complexity of distributed databases, this white paper will uncover the 10 rules you’ll want to know when managing Apache Cassandra.
Let's personalize your content