Top 4 focus areas for securing your software supply chain
CIO Business Intelligence
APRIL 24, 2024
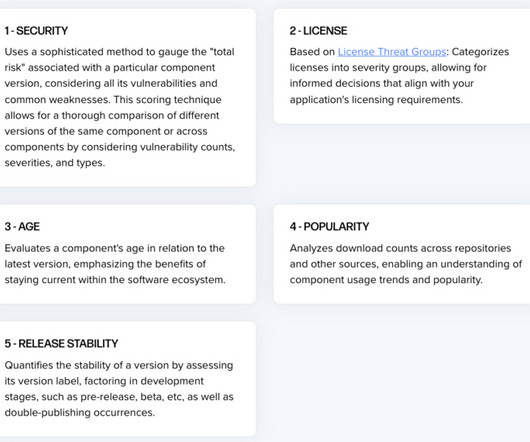
The complexity of the software supply chain (SSC) has the potential to expose your organization to greater risk than ever before. In today’s fast-paced software development landscape, managing and securing the software supply chain is crucial for delivering reliable and trusted software releases.













































Let's personalize your content