Using WireGuard on macOS
Scott Lowe
APRIL 1, 2021
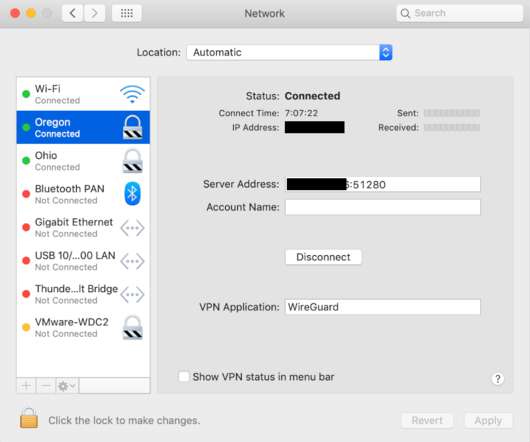
In that post, I focused on the use of Linux on both the server side (on an EC2 instance in your AWS VPC) as well as on the client side (using the GNOME Network Manager interface). Hopefully this link will take you directly there if you’re on a macOS-based system.).










































Let's personalize your content