Open-Source Tools for Pen Testing: Putting Your Technique to Work
Association of Information Technology Professional
SEPTEMBER 29, 2021
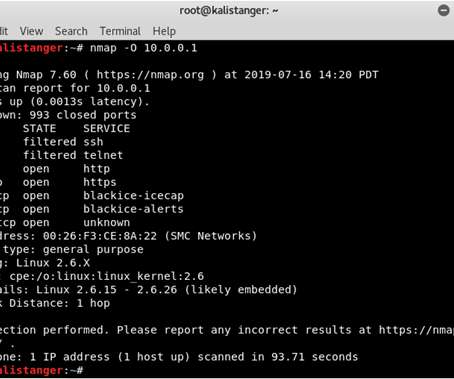
Tools and protocols go hand-in-hand. Take a look at what open-source tools work when you’re pen testing.
Association of Information Technology Professional
SEPTEMBER 29, 2021
Tools and protocols go hand-in-hand. Take a look at what open-source tools work when you’re pen testing.

Anoop
SEPTEMBER 30, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Learn How to Enable Microsoft Edge Sleeping Tabs using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
SEPTEMBER 28, 2021
Many enterprises believe that their transformation is customer-centric, but Omdia research has found that customer-centric, customer-obsessed, customer-focused are obscure terms that, unless defined clearly, can derail the success of transformation agendas.

Tech Republic Security
SEPTEMBER 27, 2021
Commercially-available malware, with minimal modification, is behind attacks against the Indian government, says Cisco's Talos security research group.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Tech Republic Data Center
SEPTEMBER 30, 2021
Microsoft has just released its most recent Windows Server platform. Check out the improved hybrid cloud features, beefed up security and improved support for large on-premises applications.

Anoop
OCTOBER 1, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Exclude OneDrive Shortcuts Sync using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
OCTOBER 1, 2021
The study, from Cisco, comes with the announcement of its New Trust Standard, a benchmark for seeing how trustworthy businesses are as they embrace digital transformation.

Tech Republic Data Center
OCTOBER 1, 2021
Organizations can derive more value from their data if data scientists and IT data analysts work together. This includes sharing that data. Here are three ways to make it happen.

Anoop
SEPTEMBER 29, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Convert WQL Queries to SQL Queries using SCCM Trick appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Cloud
SEPTEMBER 27, 2021
Microsoft Azure can provide a cloud-based file, folder and system backup recovery service at a reasonable price, if you can manage to work through a lengthy setup process.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Tech Republic Security
OCTOBER 1, 2021
The SOS program, run by the Linux Foundation, will reward developers with potentially more than $10,000 for enhancing the security of critical open source software.

Network World
OCTOBER 1, 2021
When National Cybersecurity Awareness Month (NCSAM) was launched in October 2004, it was a modest affair, offering anodyne advice to individual Americans and US businesses along the lines of making sure to update your antivirus software twice a year. Since then NCSAM has grown into an event-packed month with star-studded guest panels, annual launches in various cities (looking at you, Ypsilanti, Michigan!

Anoop
SEPTEMBER 29, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SCCM Task Sequence App Failure with Error 0x87d00267 after 2107 Update appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Cloud
SEPTEMBER 29, 2021
If you're looking for yet another cloud storage provider, one that offers a Linux desktop app, Jack Wallen believes Megasync might be exactly what you need.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Security
SEPTEMBER 28, 2021
A new phishing campaign spotted by Armorblox tried to steal user credentials by spoofing a message notification from a company that provides email encryption.

TechSpot
OCTOBER 1, 2021
The network security company said that in Q2 2021, 91.5% of malware arrived over an encrypted connection. It added that any company not examining encrypted HTTPS traffic at the perimeter will miss out on 9/10 of all malware. The data is derived from the firm’s own active WatchGuard Fireboxes.

Anoop
SEPTEMBER 28, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Easiest Method to Create SQL Queries for SCCM without Opening SQL Management Studio appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Cloud
OCTOBER 1, 2021
The only way to get extended support for 2008 versions of Windows and SQL Server is in the cloud. Here's why you should be thinking about 2012 migrations now as well.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Tech Republic Security
SEPTEMBER 27, 2021
Dubbed TangleBot, the malware can overlay financial apps with its own screens in an attempt to steal your account credentials, says Cloudmark.

TechSpot
SEPTEMBER 30, 2021
At its Search On event this week, Google revealed details about how it plans to use a technology it calls Multitask Unified Model (MUM), which should intelligently figure out what a user is searching for based on images and text, as well as give users more ways to search for.

Anoop
SEPTEMBER 27, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Remove Recently Added Apps from Start Menu using Intune appeared first on HTMD Blog #1 by Jitesh Kumar.

Tech Republic Cloud
SEPTEMBER 28, 2021
Launching initially for IGO and NGO use, Oracle Payroll Core eliminates the need to manually calculate payroll for employees working remotely outside of their own borders.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Tech Republic Security
SEPTEMBER 29, 2021
Not all organizations have a team or even staffers who can focus solely on vulnerability management, says Trustwave.
The Verge
OCTOBER 1, 2021
“Google” is the most searched term on Bing “by far,” according to a lawyer working for Google’s parent company, Alphabet. According to Bloomberg , Google made the argument while trying to get its $5 billion antitrust fine from the EU overturned, using the statistic as evidence that people use Google by choice, not force. The fine Google faces is from the European Commission, which says that Google has abused its position as the maker of Android.

Anoop
SEPTEMBER 28, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post New Method to Install SCCM Console Extensions appeared first on HTMD Blog #1 by Anoop C Nair.

Tech Republic Cloud
OCTOBER 1, 2021
SMBs that rely on NAS hardware to store data will get a performance boost in the now available, and surprisingly affordable, WD Red SN700.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Tech Republic Security
SEPTEMBER 28, 2021
The new Idle Detection API gives Chrome the ability to register whether a user is active, and has drawn concerns from privacy advocates. Here's how to disable it.

TechSpot
OCTOBER 1, 2021
One area focused on within the report is the current state of Android malware. "It is an open source system with many vendors having their own Android versions (with their own vulnerabilities and patching problems)," Eset security awareness specialist Ondrej Kubovi? told The Register.

Anoop
SEPTEMBER 27, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post 3 Free SCCM Admin Tools for Advanced Troubleshooting appeared first on HTMD Blog #1 by Anoop C Nair.

GeekWire
SEPTEMBER 28, 2021
Trevor Bedford, infectious disease scientist at Fred Hutchinson Cancer Research Center. (Photo used with permission from the John D. and Catherine T. MacArthur Foundation). In the earliest days of the COVID-19 pandemic, as we desperately flailed for reliable information to comprehend what had previously been largely unimaginable, Seattle’s Trevor Bedford was a rare source of insight.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Let's personalize your content