Announcing The Forrester Wave™: Endpoint Security, Q4 2023
Forrester IT
OCTOBER 27, 2023
Endpoint security is one of the most mature markets in cybersecurity.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 endpoint-security
endpoint-security 
Forrester IT
OCTOBER 27, 2023
Endpoint security is one of the most mature markets in cybersecurity.

Forrester IT
MAY 14, 2021
I am excited to announce The Forrester Wave™: Endpoint Security Software As A Service, Q2 2021. Although Forrester has previously published other endpoint security Waves, this is the first Endpoint Security Software Wave that exclusively focused on SaaS-delivered products and functions.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CTOvision
JUNE 30, 2021
Read why Joe Devanesan says that companies can secure their supply chains only by tackling the endpoint exposure on Tech HQ : Supply chain efficiencies were pushed to the brink during the height of the COVID-19 pandemic, and the security posture of many a supply chain experienced cracks on an unprecedented level.

Advertisement
How to secure your IT Infrastructure to help protect your business from cyberattacks. How ThreatLocker can help you mitigate cyber threats with our unique endpoint solutions. Download the eBook to learn: The essential steps you need to take to harden your Windows Servers. And more!

Forrester IT
JANUARY 21, 2021
Today’s enterprise security buyers evaluating a new endpoint security suite often begin with a security RFP layered thick with many existing endpoint security features and capabilities, including antimalware, host firewall, anti-exploit, and application control.

Anoop
APRIL 14, 2023
Read More The post Endpoint Security Reports for Tenant Attached Devices in Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link].

Tech Republic Security
JUNE 21, 2023
Cybersecurity has always been challenging, but with the cloud becoming more complex, the Internet of Things more advanced and remote work more embraced, security and endpoint management face a host of new challenges. The post Remote work and the cloud create new endpoint security challenges appeared first on TechRepublic.

CIO Business Intelligence
MARCH 6, 2024
Despite growing interest in “as a service” consumption models for everything from infrastructure to storage, most enterprises have continued to procure, maintain, and manage endpoint devices in-house. Security is a key driver. In this environment, endpoint security becomes increasingly important.

Anoop
AUGUST 4, 2023
Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link] The post New BitLocker Disk Encryption Policy for Intune Endpoint Security appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it.

Anoop
MAY 5, 2023
Read More The post Secure Android Devices using Microsoft Defender for Endpoint in Intune appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it.

Anoop
NOVEMBER 6, 2019
Sneak peak of Microsoft Endpoint Manager security topics discussed in the section hosted by Paul Mayfield, Terrell Cox, and Micro-Scott. More details about the session and Intune Endpoint Security are given below.

Anoop
JULY 20, 2022
The post Managing Security Risks of Windows Endpoints Survey Report appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Admin. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it.

Anoop
APRIL 20, 2022
The post Endpoint Security is the Most Important Pillar of Security Investments appeared first on HTMD Community Blog #1 Modern Device Management Guides - Windows 11 | SCCM | ConfigMgr | Intune | AVD | Windows 10 | Windows 365 | Cloud PC by Admin. Hello - Here is the new HTMD Blog Article for you. Enjoy reading it.

Tech Republic Security
JULY 13, 2022
The post Nearly half of enterprise endpoint devices present significant security risks appeared first on TechRepublic. Organizations are struggling to manage devices and stay ahead of vulnerabilities, patches and attacks, according to a new report from Adaptiva and the Ponemon Institute.

Tech Republic Security
MARCH 15, 2022
Symantec Endpoint Protection and Webroot Internet Security Plus 2022 are compelling security products intended to protect business systems. Learn the pros and cons of each security solution to make the best possible choice.

Tech Republic Security
MARCH 11, 2022
If you're trying to decide on endpoint protection software for your business, these two options are good choices. The post Crowdstrike Falcon vs. Avast: Endpoint security software appeared first on TechRepublic. Which one should you choose? Here is a comparison of the two.

Forrester IT
NOVEMBER 9, 2023
Recent news of Palo Alto Networks announcing intentions to acquire Talon Cyber Security demonstrates the importance of securing the browser. In Forrester’s 2022 report on browser security, we discussed enterprise browsers — a solution that Talon Cyber Security delivers, along with an extension, for protecting this modern endpoint.

Venture Beast
JANUARY 3, 2022
Learn more Bad actors continue to capitalize on the widening gaps in endpoint security that all organizations are planning to improve in 2022. chief information security officers (CISOs) and their teams are stretche… Read More.

Tech Republic Security
FEBRUARY 13, 2022
Giving employees the flexibility to be fully productive while working remotely makes it critical that businesses have endpoint security measures in place to prevent, detect and respond to the growing threat landscape while allowing employees the flexibility to work remotely.

Venture Beast
SEPTEMBER 16, 2021
Kolide, an endpoint security provider focusing on transparency, has raised $17 million in a venture funding round. Read More.

Venture Beast
OCTOBER 6, 2021
A key takeaway: Unified Endpoint Security (UES) technology platforms will manage the diverse parts of a cybersecurity tech stack. Read More.

Tech Republic Security
FEBRUARY 13, 2022
Giving employees the flexibility to be fully productive while working remotely makes it critical that businesses have endpoint security measures in place to prevent, detect and respond to the growing threat landscape while allowing employees the flexibility to work remotely.

Forrester IT
MARCH 1, 2022
Tell us about yourself! I’ve spent the last 25-plus years in the end user computing space — the world of connecting end users to their applications and data. My teenage hobby of computers has turned into my career, with my initial education in aeronautics. Whether it was seeing “WarGames” when it first came out, “hacking” […].
Venture Beast
MARCH 3, 2022
Knowing the current configuration and condition of every endpoint asset helps to keep patches current and maintain endpoint security. Read More.

CTOvision
DECEMBER 10, 2020
The two companies will combine their solutions, bringing endpoint protection and attack disruption together […]. Attivo Networks and SentinelOne have teamed up to combine cybersecurity defences and stop attackers in their tracks.

Computer Weekly
OCTOBER 19, 2017
Endpoint devices, the cloud and people will be the security control points of the future, according to the chief of security firm McAfee
Venture Beast
MARCH 3, 2022
Endpoint security is accelerating thanks to the aggressive use of AI and ML by bad actors intent on wreaking havoc for financial gain. Read More.

CIO Business Intelligence
NOVEMBER 23, 2022
A recent spate of high-profile security breaches at some of the largest enterprises in Australia has reminded everyone of the importance of security. The biggest challenge when it comes to cyber crime is that there are so many different security risks to manage. vPro also boosts security for virtualised environments.
Venture Beast
MARCH 3, 2022
Defining a business case for endpoint security needs to quantify as many benefits and costs beforehand as possible if it’s going to succeed. Read More.

Computer Weekly
AUGUST 3, 2017
IT professionals are focusing on endpoint security in the face of custom malware that is bypassing traditional perimeter defences, a survey shows

Anoop
OCTOBER 18, 2017
Security of endpoints is a high priority for all the organizations. Windows 10 migrations and endpoint security should be aligned with the goals of each organization. IT Pros are responsible for maintaining both Windows 10 and security strategies.

Computerworld Vertical IT
FEBRUARY 12, 2021
Enterprises seeking tools with which to improve endpoint security for the new remote working business environment may want to spend a little time considering the Apple Watch. Access all areas. My argument is simple: Apple’s growing place in the enterprise means its complementary ecosystems can help support your business.

CIO Business Intelligence
APRIL 28, 2022
A few decades ago, corporate endpoints consisted mainly of stationary PCs glued to the desk. Back then, protecting endpoints involved anti-malware tools that sniff out suspicious files based on static signatures. With most employees working on-site, the focus gradually shifted from endpoints to perimeter.

Tech Republic Security
AUGUST 16, 2022
If you’re considering a third-party audit like SOC 2 or ISO 27001, you should be prepared to answer some tough questions about endpoint security. Kolide is an endpoint security tool for Mac, Windows, and Linux devices that does things MDMs can’t. appeared first on TechRepublic.

Forrester IT
FEBRUARY 5, 2020
When the endpoint detection and response (EDR, which was also referred to as endpoint threat detection and response, or ETDR, at the time) market was getting started, there was a lot of pushback, ranging from privacy concerns to what the acceptance of a second security agent on endpoints would be (apparently, it was never going […].

Forrester IT
AUGUST 19, 2022
Learn how endpoint security has been impacted by the more to anywhere work and what steps security pros can take in this preview of the Security & Risk event.
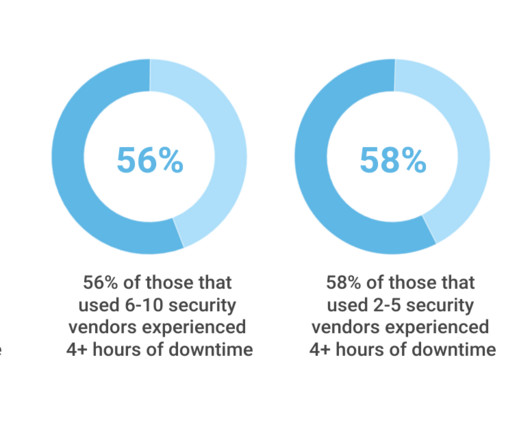
IT Toolbox
JUNE 13, 2023
Extended detection and response (XDR) collects, correlates, and aggregates telemetry data from multiple security layers and products, including servers, network appliances, cloud workloads, endpoints, and applications. The post Building a Simplified Approach to Security with XDR appeared first on Spiceworks.

CTOvision
JULY 14, 2021
Read Tyler Logtenberg explain how companies can improve their supply chain security through threat intelligence from surface, deep and dark web on Security Intelligence : It would be comforting if the only cyber-risks organizations had to worry about were the ones that smacked up against their firewall and endpoint security solutions.

Venture Beast
APRIL 23, 2021
ANALYSIS: Imagine that every endpoint on an IT network is self-aware — it knows if it’s under attack and immediately takes steps to thwart the attack. Join Transform 2021 this July 12-16. Register for the AI event of the year. This… Read More.

CTOvision
OCTOBER 12, 2020
According to new data released by Cybersecurity Insiders, 72% of organizations experienced an increase in endpoint and IoT security incidents in the last year, while 56% anticipate their organization will […].

Forrester IT
DECEMBER 5, 2018
The endpoint detection and response (EDR) market represents the direction of endpoint security, yet the state of endpoint efficacy testing has been underwhelming. Antimalware testing has become a standard part of the endpoint […].

CIO Business Intelligence
JULY 11, 2022
With the proliferation of hybrid clouds, SD-WAN, and a plethora of connected devices and digital platforms, it’s becoming increasingly challenging to ensure end-to-end security is in place. As IT and security continue to converge, unfortunately, the teams needed to do the work are still facing significant talent shortages.
Forrester IT
DECEMBER 8, 2021
What comes up in conversations on endpoint detection and response (EDR) lately? It’s impossible to deny that extended detection and response (XDR) has taken hold of the security market as the successor to EDR. A slightly different *DR.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content