Mobile private network deployment growth brings wins for telcos
TM Forum
AUGUST 12, 2021
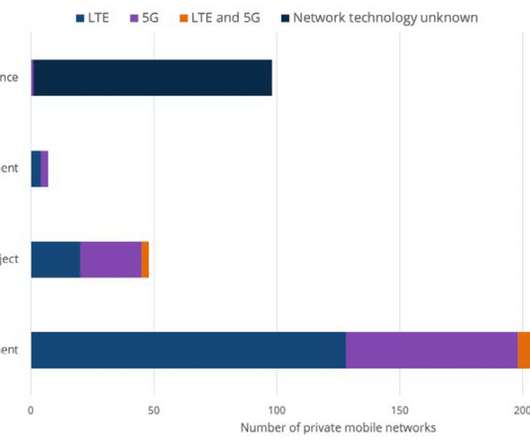
The report 79 identified manufacturers holding suitable licences or piloting or deploying LANs -- or probable LANs (the report also acknowledges the difficulty of measuring a market in which deals are often not made public). The research group Delloro, for example, expects revenues from. whereas ABI sees much faster growth.


























Let's personalize your content