Legitimacy and Decentralized Systems
Phil Windley
APRIL 26, 2021
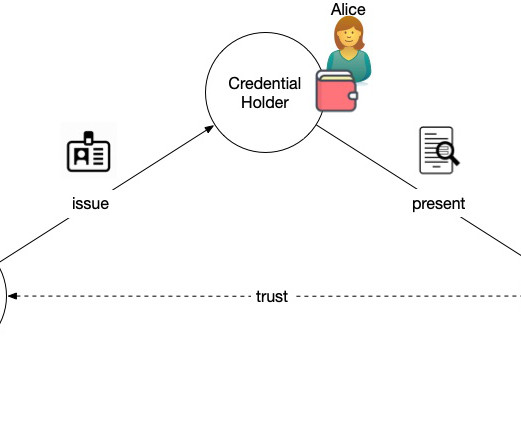
It all comes down to legitimacy. In The Most Important Scarce Resource is Legitimacy , Vitalik Buterin, the creator of Ethereum, discusses why legitimacy is crucial for the success of any decentralized endeavor. From The Most Important Scarce Resource is Legitimacy Referenced 2021-04-26T14:46:43-0600.


























Let's personalize your content