Rubrik Acquires Laminar: Data Resilience And Security Join Forces
Forrester IT
AUGUST 22, 2023
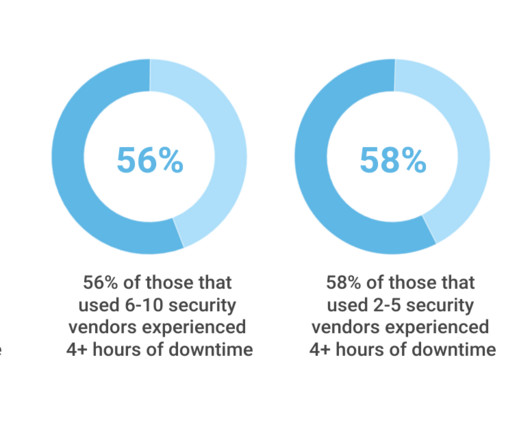
As security threats increase, data protection and security practices continue to merge. Data resilience firm Rubrik recently announced its acquisition of Laminar, a data security posture management (DSPM) vendor. Modern Data Resilience Is Increasingly A Cybersecurity Issue […]
















































Let's personalize your content