The LLM Misinformation Problem I Was Not Expecting
SecureWorld News
DECEMBER 21, 2023
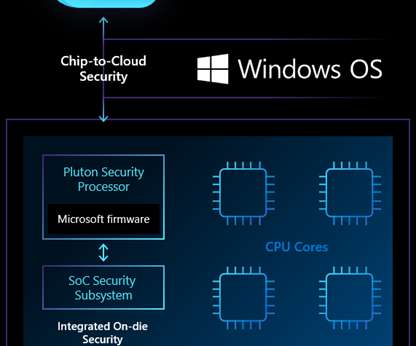
In that particular case, however, they sought supporting materials in a manner similar to the use of an internet search engine. Misidentifying AI libraries/software as operating systems In one example, I saw students reference descriptions of what might be AI-related libraries or software as operating systems.













































Let's personalize your content