Generative AI: Balancing security with innovation
CIO Business Intelligence
SEPTEMBER 7, 2023
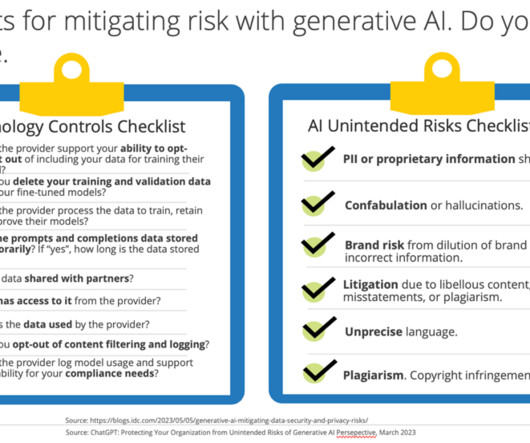
Additionally, related issues during use are risk of hallucinations and prompt engineering. Conclusion As the Chief Information Security Officer (CISO) at Discover, I am both excited and sober about how generative AI will change the fintech landscape in the coming years. Exploiting technology vulnerabilities.






















Let's personalize your content