Mitigating Advanced Threats with Scalable and Automated Malware Analysis: An interview of Chad Loeven and Mike Hylton
CTOvision
JANUARY 9, 2022
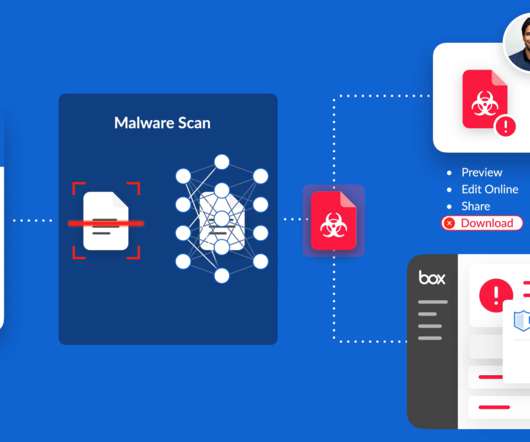
Scalable automated malware analysis has become a critical component of enterprise defense. When properly implemented it can be key to mitigating malware threats that otherwise bypass perimeter defenses. It is based on an […].


















































Let's personalize your content