How To Secure Your Business From the Endpoint to the Cloud
IT Toolbox
MAY 8, 2023
Are you overlooking the most common security risks? The post How To Secure Your Business From the Endpoint to the Cloud appeared first on Spiceworks.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

CTOvision
AUGUST 31, 2020
Read Chris Foster list five critical cloud security challenges and how to overcome them on Help Net Security : Today’s organizations desire the accessibility and flexibility of the cloud, yet […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Human-Centered Cyber Security Training: Driving Real Impact on Security Culture
Don’t Get Left Behind: Leveraging Modern Product Management Across the Organization

Network World
MAY 28, 2024
WPA3 is the latest iteration of the Wi-Fi Protected Access (WPA) standard, succeeding WPA2, which has been the de facto security protocol for wireless networks for nearly two decades. This new standard addresses the security vulnerabilities inherent in WPA2, while adding some brand-new security functionality. authentication.

Advertisement
To address this, a next-gen cloud data lake architecture has emerged that brings together the best attributes of the data warehouse and the data lake. Read this whitepaper to learn: How this “no data copy” approach dramatically streamlines data workflows while reducing security and governance overhead.

IT Toolbox
JUNE 19, 2023
The secret to managing rising cloud storage costs in an era of data overload. The post How to Prioritize Cost Optimization for Cloud Storage Investments appeared first on Spiceworks.

Information Week
AUGUST 28, 2023
Cloud users keep making the same security mistakes. Here’s how you can get your team to prioritize cloud defense.

CTOvision
MAY 16, 2019
Read Matthew Chiodi list top four cloud security concerns and how to address them on Palo Alto Networks Blog : The cloud can be overwhelming. Counter to the structured and disciplined rigor of old-school, waterfall, data-center-centric application development, there’s code being deployed in a nearly continuous fashion.

Tech Republic Cloud
DECEMBER 6, 2022
Learn how to enable Defender for Cloud, the differences between the basic and enhanced versions, and what they can do for your security posture. The post How to enable Microsoft Defender for Cloud plans through the Azure portal appeared first on TechRepublic.

CTOvision
DECEMBER 2, 2019
Read Louis Columbus explain how to excel at secured cloud migrations through shared responsibility on Cloud Computing : These and many other fascinating insights are from the recent Centrify survey, Reducing Risk in Cloud Migrations: Controlling Privileged Access to Hybrid and Multi-Cloud Environments, downloadable here.

CIO Business Intelligence
FEBRUARY 7, 2023
For as long as organizations have been interested in moving resources to the cloud, they’ve been concerned about security. That interest is only getting stronger as cloud usage grows – making it a perfect topic for the latest #CIOTechTalk Twitter chat. It’s a timely topic given the rapid cloud migration currently underway.

Forrester IT
MAY 1, 2024
Forrester announces the opening call for our annual Security & Risk Enterprise Leadership Award. This award recognizes organizations that have transformed the security, privacy, and risk management functions into capabilities that fuel the organization’s long-term success. Learn more about the award and how to apply here.

Information Week
JULY 17, 2023
Cloud presents new security challenges regularly. This collection of articles from the past year includes expert advice and experiences from peers on how to create an effective enterprise cloud strategy.

Information Week
MARCH 10, 2022
Cloud security is a shared responsibility between the businesses leveraging the cloud and their cloud service providers. Here are tips on how to build and maintain robust security models.

CTOvision
MARCH 25, 2020
Read Gadi Naor’s article about securing your Kubernetes deployments against cyberattacks on Dark Reading : At a time when almost every company is to some degree a software company, digital transformation and cloud adoption are not just strategic but critical to enterprise success.

Association of Information Technology Professional
JANUARY 20, 2021
To benefit from the cloud, you must be able to anticipate these common security flaws and know how to mitigate them.

TM Forum
NOVEMBER 13, 2022
With the introduction of 5G, Open RAN and cloud infrastructure, telecom is facing the reality of latest attack surfaces and exposure to sophisticated external attack strategies. Required defenses are relatively new to telecom but not new to other industries that have been securing open interfaces and cloud-native operations for many years.

CTOvision
JULY 27, 2020
Read Manish Mistry list 10 steps to ensure Amazon AWS security on DevOps: As more companies embrace the cloud, security is becoming a more significant challenge. Irrespective of size, organizations […].

CIO Business Intelligence
JUNE 3, 2024
A new surge of enthusiasm surrounds a strategic framework poised to simplify the management of cloud expenses and help companies lower their IT costs — it’s called FinOps, a portmanteau of the words Financial and DevOps. Public cloud infrastructure seems to be a place where you can “check out any time you like, but you can never leave.”

Kitaboo
MAY 7, 2024
With these crimes becoming a pressing concern in today’s age, there is a growing need for the implementation of stringent security measures. How to Protect ePUB from Copying: Implement These Security Measures DRM Password Protection Editing Restrictions Google Alerts Official Copyright Notice DMCA Takedown Notice II.

Tech Republic Cloud
MAY 16, 2023
Migrating your company’s data and operations to Google Cloud offers easier access, better security and more. The post Learn how to use Google Cloud for your business for only $40 appeared first on TechRepublic.

Tech Republic Security
MARCH 6, 2024
Learn how to use Norton Secure VPN with our in-depth tutorial. Having a hard time getting started with Norton VPN?

CIO Business Intelligence
NOVEMBER 6, 2023
The business world is rapidly continuing its digital transformation and relying on cloud-based solutions. This makes it more critical than ever to adopt strong security measures to protect sensitive information and infrastructure.

CIO Business Intelligence
JANUARY 22, 2024
The remote work revolution has pushed companies to rethink their security and data protection practices amidst hybrid work and cloud environments. trillion by 2025, as cyber risk management has not kept up with digital transformation posing serious risks to organizations’ security and revenue.

IT Toolbox
AUGUST 9, 2022
Organisations are now operating entire businesses in the cloud and benefiting from faster, more efficient, reliable, secure and scalable computing, but many with legacy architecture and code are finding themselves competing with businesses that have been ‘born in the cloud’ and lacking the agility of their competitors.

CTOvision
JANUARY 14, 2020
Read Jon Oltsik explain how to move your security operations to the cloud on CSO Online : It’s also important to remember that these security operations challenges are exacerbated by the ongoing cybersecurity skills shortage as there just aren’t enough skilled bodies to throw at problems.

Tech Republic Cloud
MARCH 30, 2022
Many professionals, including consultants and freelancers, must often work with both Apple iCloud and Microsoft OneDrive cloud services. See how to securely transfer files between the two platforms. The post How to secure and move files between iCloud and OneDrive appeared first on TechRepublic.

Tech Republic Security
MAY 25, 2023
As organizations have migrated to cloud-based infrastructure and office platforms like Microsoft 365 and Google Workspace, they’ve seen clear benefits: easier collaboration, greater agility, and lower costs and maintenance related to infrastructure. The post The Essential Guide to Cloud Email Security appeared first on TechRepublic.

Tech Republic Cloud
FEBRUARY 7, 2022
Creating a strategy for big data storage is important for your costs, security and ease of use. The post Housing your big data in the cloud: Multicloud, hybrid cloud or on-premises? How to decide appeared first on TechRepublic. Here are some things to consider when making a plan.

Forrester IT
JUNE 21, 2023
Forrester is thrilled to announce its inaugural Security & Risk Enterprise Leadership Award, which will recognize security organizations that have transformed the security, privacy, and risk management functions to fuel long-term success. Learn how to apply here.

CIO Business Intelligence
JULY 17, 2023
Small- and medium-sized businesses and enterprises have accelerated their move into the cloud since the global pandemic. The Infrastructure-as-a-Service (IaaS) cloud computing model enables remote working, supports digital transformation, provides scale, increases resilience, and can reduce costs. Watch on-demand here.

CIO Business Intelligence
MAY 14, 2024
Private cloud providers may be among the key beneficiaries of today’s generative AI gold rush as, once seemingly passé in favor of public cloud, CIOs are giving private clouds — either on-premises or hosted by a partner — a second look. The excitement and related fears surrounding AI only reinforces the need for private clouds.

Kitaboo
FEBRUARY 22, 2024
While this is just one facet of a comprehensive eBook protection strategy, combining such measures with advanced technologies and vigilant monitoring can significantly enhance the security of your digital literary creations in the ever-evolving digital landscape. Guide: How to Build an eBook Store Download Now!

Tech Republic Cloud
MAY 21, 2020
The Identity and Access Management system in Google Cloud Platform is vital to the overall security of your business. Learn how to establish IAM credentials from the console screen.

CTOvision
JANUARY 27, 2018
Cloud Access Security Brokers (CASB) have been hot for the last 5 years. It has gotten to the point where every firm is either using one, evaluating one, or studying how to use them.

Forrester IT
FEBRUARY 28, 2023
I’ve been working with a long list of financial services companies from various subsectors on their cloud strategies. Each wants to know how to best take advantage of cloud while meeting stringent (and shifting) regulatory requirements. It’s been a long road for financial services and cloud.

CIO Business Intelligence
JANUARY 9, 2024
Achieving and sustaining compliance with the Payment Card Industry Data Security Standard (PCI DSS) is a daunting challenge for hotels because they handle many complex payment business cases. See the PCI Security Standards Council (SSC) Requirements and Testing Procedures , Version 4.0 Four recommended steps in the PCI DSS v4.0
CIO Business Intelligence
JUNE 3, 2024
Cloud doesn’t just open the door to enabling advanced technologies like AI, hyper-automation, and big data analytics – it unlocks a complex realm of costs and expense management problems that can threaten innovation and its financial sustainability. This is the first and most essential step for mastering today’s cloud economics.
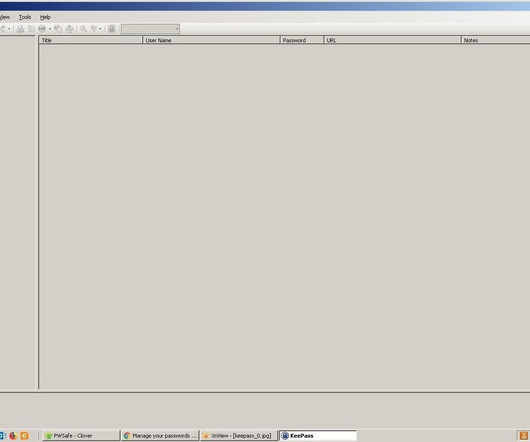
Tech Republic Security
JANUARY 31, 2024
This tutorial will guide you on how to use KeePass to manage and secure your passwords. Learn how to set it up and make the most of its features.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?




Let's personalize your content