Finding your ideal VMware Disaster Recovery and Migration Cloud Provider
CIO Business Intelligence
SEPTEMBER 23, 2022
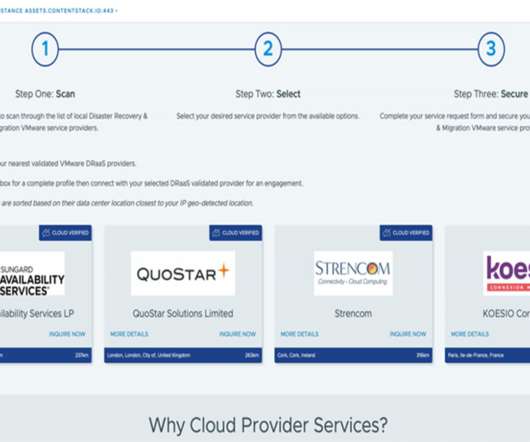
Cloud Provider Services capability enables you to choose your ideal, closest Disaster Recovery and Migration partner based on your vSphere console IP location and the nearest Disaster Recovery partner data center. Step 3: Secure: Complete your service request form to secure the services of your chosen cloud provider.







































Let's personalize your content