9 Ways to Improve IT and Operational Efficiencies in 2020
Information Week
JANUARY 2, 2020
Facing economic uncertainty, many IT leaders are looking to become more efficient while also investing in the latest technology.

Information Week
JANUARY 2, 2020
Facing economic uncertainty, many IT leaders are looking to become more efficient while also investing in the latest technology.

CTOvision
JANUARY 2, 2020
Read Carlos Asuncion explain how you can prevent hackers from targeting your mobile payment apps on Dark Reading : Consumers love paying for goods and services with their smartphones. But as more retailers release their own mobile apps with in-store payment options, the threat of fraud must be carefully considered. Retailers offering in-store purchasing through […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Week
DECEMBER 31, 2019
Bias can result in undesirable AI outcomes. A recent DataRobot survey says organizations are most concerned about its impact on trust and their reputations.

Forrester IT
JANUARY 2, 2020
It’s that time of year. When folks make up their minds that things are going to change. The gym is full of new members who are eager to get into their journey towards some other semblance of better health, or a beach body, or some change that they desire. Others are in that annual state […].

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Social, Agile and Transformation
DECEMBER 30, 2019
Every once and a while, I draw inspiration from movies and actors/actresses. I have a post paying tribute to the great movie. What about Bob? Baby Steps - A Guide to Digital Transformation. I have another post comparing executive meetings with a classic Darth Vadar scene from The Empire Strike's Back. My two personal favorite movie posts are product management advice from the Tom Hanks movie.

CTOvision
JANUARY 1, 2020
The Dali Lama just posted some very wise thoughts for our consideration: Time never stands still, it’s always moving on. The past is beyond our control, but the future is still in our hands. To shape it we must use our intelligence and make an effort. We can change our circumstances. Becoming demoralized is of […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Forrester IT
JANUARY 3, 2020
The best New Year’s resolution? Become machine-learning-literate! It’s good for your organization, your career, and the sanity of your data scientists. See the new “Shatter The Seven Myths Of Machine Learning” report below for a mini course on machine-learning fundamentals and terminology.
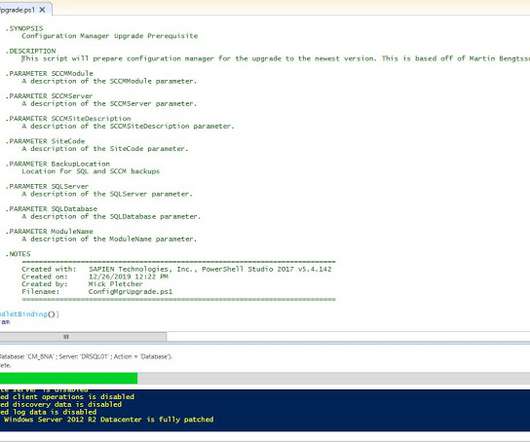
Mick's IT Blog
JANUARY 2, 2020
With the advent of Microsoft Endpoint Manager Configuration Manager 1910, I started researching the upgrade requirements. I happened to run into a great blog post by fellow MVP Martin Bengtsson on what should be done before the upgrade takes place. That got me to thinking that most of the tasks he listed can be automated with PowerShell. The script below will automate the following tasks from his list of prerequisites: Backs up the cd.latest directory to the specified UNC path Disables the follo

CTOvision
DECEMBER 30, 2019
The federal government’s leading tech media brand FedScoop has just published an insightful look inside Palantir’s support to some of the Army’s most critical mission needs. The report dives into a recent contract award that aims to bring together a wide range of disparate data from unique and often totally disjointed systems to provide decision-makers […].

Information Week
JANUARY 3, 2020
Here are five key techniques to support and encourage entrepreneurship in your employees -- while simultaneously keeping everyone moving in the right direction.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Forrester IT
DECEMBER 30, 2019
In October 2019, our team published its Predictions 2020: B2B Marketing And Sales, and in late December we recorded Webinar: B2B Marketing And Sales Predictions 2020: A Conversation With The Analysts Who Made Them. In the waning hours of 2019, Caroline Robertson and I took the opportunity to double-click into our sales enablement predictions. What […].

Anoop
JANUARY 3, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Great to start the year 2020 by announcing that this blog (www.anoopcnair.com) is part of Feedspot Top 20 SCCM blogs to follow in the year 2020. 😍😍😍👌👌 Subscribe to this blog NOTE! – Feedspot published this list of blogs in SCCM category even though Microsoft changed the name of SCCM to MEMCM.

CTOvision
DECEMBER 30, 2019
A critical flaw has been discovered in two Citrix products, placing 80,000 companies in 158 countries at risk. The easily exploitable vulnerability could allow attackers to obtain direct access to a company’s local network and to access a company’s credentials. It could also be used to launch denial of service and phishing attacks and to implant malware […].

Tech Republic Security
JANUARY 2, 2020
E-commerce sites are trying to keep up with sophisticated skimming schemes, but chances are your credit card information will still be compromised. A security expert offers advice.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Forrester IT
DECEMBER 31, 2019
Is your firm ready for the roaring twenties? Nigel Fenwick predicts the winners in the next decade will be the businesses that master digital product management.

Anoop
DECEMBER 30, 2019
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. This is the 3rd article of the Bitlocker series. Links to previous parts are mentioned below. Give them a read if you have not yet! Part 1 – Bitlocker Unlocked with Joy – Behind the Scenes Windows 10 Part 2 – Device Encryption – Bitlocker made Effortless Today in this post, we will be talking […].

CTOvision
JANUARY 2, 2020
As 2019 winds down, every news media and technology site is pausing to reflect on the biggest trends of the past year. Some aspects of robotics and artificial intelligence are advancing rapidly; others, not so much. What should AI and robotics developers recall as they prepare for a new year? Sudhir Jha, senior vice president […].

Mick's IT Blog
DECEMBER 31, 2019
I wanted to install the Configuration Manager PowerShell module on my admin machine. After investigating a little, the module does not exist in the Microsoft PowerShell gallery. The PowerShell script below will create the module directory under the WindowsPowerShellmodule directory within %PROGRAMFILES%. It will then copy over all of the necessary files.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Forrester IT
DECEMBER 30, 2019
My colleagues Danny Mu, Guannan Lu and I attended Alibaba ONE Business Conference on December 18 in Hangzhou. The conference attracted 2,000 business leaders from brands across industries and focused on how Alibaba enables brands’ business growth with its digital ecosystem, data and technology capabilities, and business methodologies. Alibaba wrapped these tools, methods, and capabilities […].

Tech Republic Security
DECEMBER 29, 2019
If you find port 80 is a security risk on your network, you can change the Apache listening port to something non-standard.

CTOvision
DECEMBER 30, 2019
Read Rob Csernyik’s article about how to invest in the Industrial Internet of Things on Barrons : Smart home products like Google Nest, Ring, and smart refrigerators have kept consumers ahead of the curve of the Internet of Things (IoT), which refers to the interconnection of everyday objects via the internet. As household and commercial […].
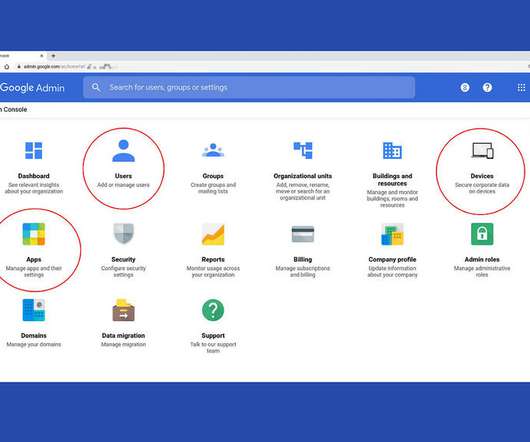
Tech Republic Cloud
JANUARY 2, 2020
Review your organization's G Suite settings to ensure they reflect company user, device, and app needs.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Forrester IT
DECEMBER 30, 2019
I believe most people who own credit cards have experienced fraud or false positives (non-fraud transaction declined), so did I. Three months ago, I have experienced an overseas credit card fraud with amount around 3,000 USD and my bank is still investigating the case now. What gave me a deeper impression was the complicated procedures […].

Tech Republic Data Center
DECEMBER 31, 2019
Your best competitive asset might just be the one you already own. Walmart is using edge computing to compete against Amazon with data centers. Could your company use its assets to try something new?

CTOvision
DECEMBER 30, 2019
Despite the escalation of cybersecurity staffing and technology, enterprises continue to suffer data breaches and compromises at an alarming rate. How do these breaches occur? How are enterprises responding, and what is the impact of these compromises on the business? This report, one of three to come out of Dark Reading’s annual Strategic Security Survey, […].
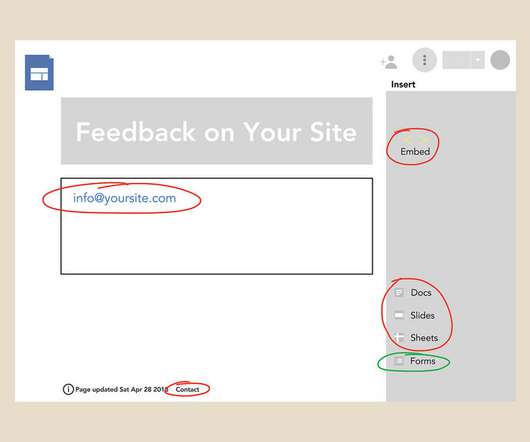
Tech Republic Cloud
JANUARY 2, 2020
Learn five ways to assemble information via a Google Site in this tutorial.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Forrester IT
DECEMBER 30, 2019
A week ago before Christmas, PayPal has officially finished its acquisition of a Chinese licensed payment company GoPay, a deal has started since the end of September. This deal signals PayPal’s official entry to China’s domestic payment market and made it the first foreign payment company to own the domestic payment license. I have followed […].

Galido
JANUARY 2, 2020
Information Technology Blog - - 10 Tips for the Localization of Your Content in 2020 - Information Technology Blog. Modern business has the best chance of growing to a global level. Never before has it been so easy to connect people from all over the world with leading brands using online technologies, and never before has it been so easy to give them the experience they want – with the help of developed logistics and delivery systems.

Information Week
JANUARY 2, 2020
Skills like communication, observation, empathy and logical thinking are key for developing the next-gen of leadership and equipping employees for the future.

Tech Republic Security
JANUARY 2, 2020
E-commerce sites are trying to keep up with sophisticated skimming schemes, but chances are your credit card information will still be compromised. A security expert offers advice.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Let's personalize your content