Why IT Leaders Should Make Cloud Training a Top Priority
Information Week
APRIL 14, 2021
As IT operations continue drifting into the cloud, it's important to ensure that organization personnel keep pace with the latest skills and practices.

Information Week
APRIL 14, 2021
As IT operations continue drifting into the cloud, it's important to ensure that organization personnel keep pace with the latest skills and practices.

CTOvision
APRIL 12, 2021
Decentralized smart contracts platform, Avalanche, has integrated with The Graph to expand querying and indexing on the platform. According to a press release shared with Coin Rivet, developers building on Avalanche can easily query custom on-chain data requests, without having to run a full node, via subgraphs, which are indexes of specifically-defined blockchain data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Forrester IT
APRIL 14, 2021
The future fit challenge applies today, not just tomorrow CIOs and technology leaders have a core objective to develop and improve the technology foundations and innovation their firms need to win, serve, and retain customers. They must also enable their employees with the capabilities to achieve this customer obsession in an efficient and effective way. […].

Social, Agile and Transformation
APRIL 15, 2021
CIO and IT leaders have the greatest opportunities to modernize their enterprise platforms, change the culture, and deliver digital business transformations. The secret is out – while first-era digital transformations were driven by improving customer experiences and leading the organization to be more data-driven, all roads on the customer journey map lead to.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Association of Information Technology Professional
APRIL 14, 2021
Getting an IT certification is an investment in your career. But with every investment comes a cost. Here are seven ways to get a voucher discount.

CTOvision
APRIL 12, 2021
According to a recent report by Total Processing, Ethereum (ETH) is the most-watched cryptocurrency on YouTube. The top altcoin has clocked over 231 million views, even more than Bitcoin. In contrast, Bitcoin has a little under 200 million views. Other top-ranking cryptos like LINK, Cardano, and Ripple achieved 45 million, 43 million, and 38 million views […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.
Social, Agile and Transformation
APRIL 12, 2021
AIOps may be the most important emerging capability for IT Operations teams. For the first time, IT has scalable tools to manage complex infrastructure, applications, databases, and devices. What's driving the business need for AIOps? It's the many factors driving organizations to invest in technologies, including digital transformation, customer/employee.

Association of Information Technology Professional
APRIL 16, 2021
With the advent of sophisticated data centers and cloud implementations, IT pros need to know how to automate tasks with tools like Ansible.

CTOvision
APRIL 12, 2021
Read Jillian Hamilton explain how the Palantir Technologies $89.9 million contract with the U.S. National Nuclear Security Administration could help the job landscape on Clearance Jobs : In a cleared market, passive candidates with an active clearance are a recruiters dream. It pays to keep your eye on the job landscape so that you’re ready […].

Forrester IT
APRIL 12, 2021
How long does your organization retain customer, employee, and sensitive corporate data, and how do you go about disposing of it? In the absence of explicit regulatory mandates, when and how to delete different types of records and personal data can become a tug-of-war between line of business, legal, and security teams. There are consequences of improper deletion and disposal, as well as excessive retention.

Advertiser: GEP
Procurement and supply chain leaders are presented with their fair share of challenges, with a host of tools and strategies to resolve them. That said, what’s the best path forward to leverage this year’s trends? In this recap of a recent GEP-WBR webinar, 7 Leadership Themes for Procurement & Supply Chain Leaders in 2024, GEP’s Pramod Sethumadhavan explores seven vital leadership trends that will help guide procurement and supply chain decision-makers.
Anoop
APRIL 16, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Read More. The post Best Guide to Enable ConfigMgr Enhanced HTTP Configuration | SCCM | eHttp appeared first on HTMD Blog by Anoop C Nair.

Association of Information Technology Professional
APRIL 13, 2021
Find out where IT pros earn the most money and how you can increase your salary this year.

CTOvision
APRIL 12, 2021
Read explain how Chainlink’s modular oracle for Substrate framework can give greater informational access to De-Fi applications, users and developers on Bitcoin News : As demand for smart contracts climbs, Chainlink’s modular oracle for the Substrate framework aims to power developers and defi applications with trusted off-chain information and pricing data needed to attract projects […].
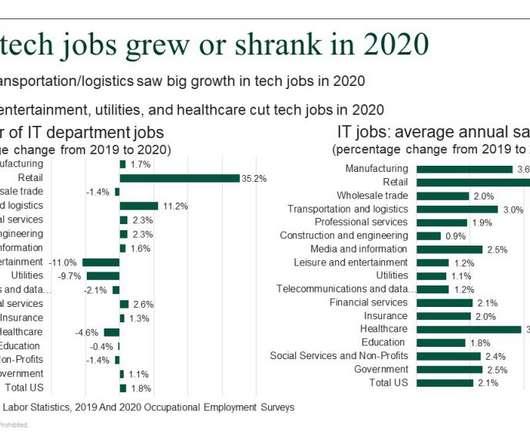
Forrester IT
APRIL 14, 2021
The US Bureau of Labor Statistics on March 31 released its 2020 Occupational Employment Survey. We use this data for our estimates and forecast of US business and government spending on tech staff, utilizing both the data on tech jobs by industry and on average annual salaries for different tech positions. But the OES survey […].

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Information Week
APRIL 16, 2021
Machine learning models are not infallible. In order to prevent attackers from exploiting a model, researchers have designed various techniques to make machine learning models more robust.

Tech Republic Cloud
APRIL 13, 2021
After Elastic decided to relicense Elasticsearch under the non-open source Server Side Public License, Amazon Web Services open sourced the old code into its own fork, OpenSearch.

Anoop
APRIL 12, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Read More. The post Device Configuration Workload Switch ConfigMgr Co-Management | SCCM appeared first on HTMD Blog by Anoop C Nair.

Forrester IT
APRIL 13, 2021
Learn the key design principles to making your IT operating models more adaptive.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Information Week
APRIL 12, 2021
Recent compromises to cloud services and increased data privacy regulations can negatively impact the bottom line for businesses with nationwide operations.

Tech Republic Security
APRIL 12, 2021
The cybersecurity poverty line is a term that can help companies understand security gaps and build better awareness. Learn more about it and how it applies to your organization.

Anoop
APRIL 13, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Read More. The post How to Remove SCCM Client from Provisioning Mode | ConfigMgr appeared first on HTMD Blog by Debabrata Pati.

Tech Republic Cloud
APRIL 13, 2021
Raspberry Pi 4 owners can now train their own custom models using Edge Impulse's cloud-based development platform for machine learning on edge devices.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.

Association of Information Technology Professional
APRIL 14, 2021
Discover how and why your organization should become PCI-DSS compliant.

Tech Republic Security
APRIL 14, 2021
From remote work and social media to ergonomics and encryption, TechRepublic has dozens of ready-made, downloadable IT policy templates.

Anoop
APRIL 14, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Read More. The post Best ConfigMgr Secondary Server Upgrade Step by Step Guide | SCCM appeared first on HTMD Blog by Anoop C Nair.

Tech Republic Cloud
APRIL 16, 2021
If you're looking for job security and salaries averaging over $100,000, it's a good time to gain cloud skills.

Advertiser: GEP
Generative AI goes beyond just automating tasks and providing real-time answers. Did you know that implementing generative AI reduces sourcing cycle times and allows for faster decision-making across procurement operations? In this whitepaper — Next-Gen Procurement: Transforming Processes With the Power of Generative AI — experts reveal how the strategic application of generative AI within procurement processes is paving the way for groundbreaking improvements.
Information Week
APRIL 13, 2021
The CIO-CFO dynamic has undergone some changes over the past 10 years. What are these changes and how do they influence corporate dynamics?
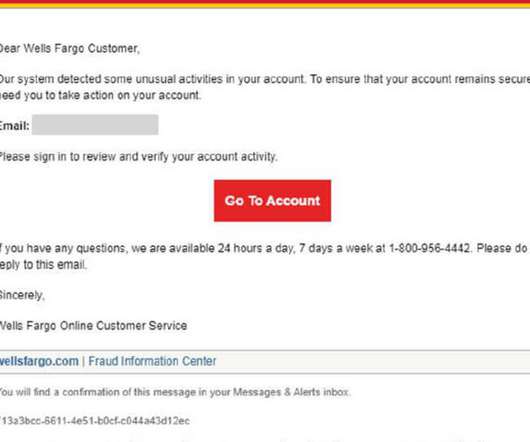
Tech Republic Security
APRIL 15, 2021
The banks are being exploited in attacks targeting people filing taxes, getting stimulus checks and ordering home deliveries, says Check Point.

Anoop
APRIL 15, 2021
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Read More. The post ConfigMgr Collection Full Incremental Evaluation Status Summary from Console | SCCM appeared first on HTMD Blog by Anoop C Nair.

Network World
APRIL 16, 2021
A set of vulnerabilities in TCP/IP stacks used by FreeBSD and three popular real-time operating systems designed for the IoT was revealed this week by security vendor Forescout and JSOF Research. The nine vulnerabilities could potentially affect 100 million devices in the wild. Nucleus NET, IPNet and NetX are the other operating systems affected by the vulnerabilities, which a joint report issued by Forescout and JSOF dubbed Name:Wreck.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Let's personalize your content