How to Block Incoming and Outgoing Network Connections Using the Windows Firewall
TechSpot
NOVEMBER 7, 2023
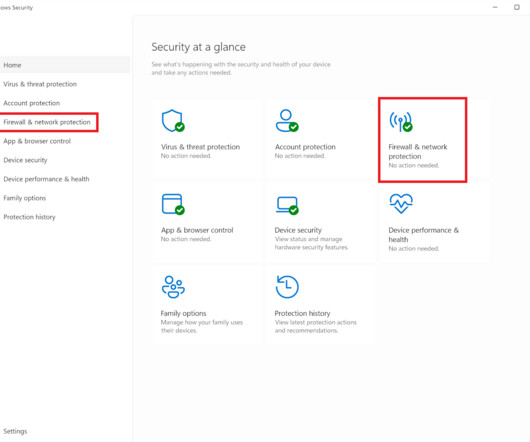
In today's world of permanent Internet connectivity, a firewall is an essential component of your device's security. Master the Windows 11 firewall with our handy guide on setting up custom blocks for incoming and outgoing traffic. Read Entire Article













































Let's personalize your content