How to build a successful digital marketplace
TM Forum
JUNE 10, 2022
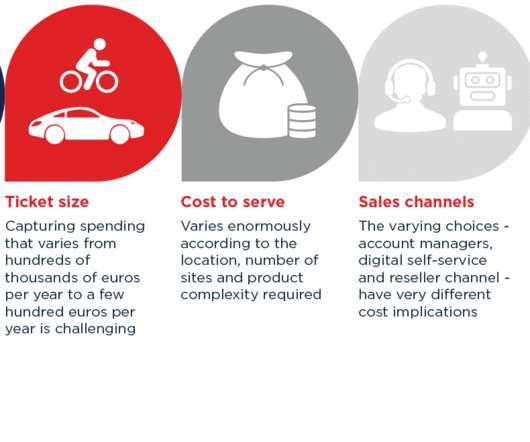
Digital marketplaces are a hot topic as communications service providers (CSPs) seek new revenue opportunities, especially in B2B markets. Operators’ common goal is to offer increasing value to businesses beyond connectivity, phones and network devices.






















Let's personalize your content