What The Massive US CHIPS Act Means To You
Forrester IT
AUGUST 9, 2022
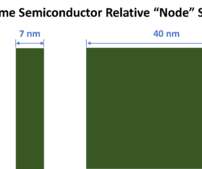
President Biden just signed CHIPS for America Act into law, as part of a larger $280B CHIPS and Science Act appropriation. This “CHIPS Act” allocates $54.2 billion in funding to support US domestic technology innovation, primarily aimed at the semiconductor industry. Much of the lobbying that brought this act to reality is focused on national […].









































Let's personalize your content