How to Protect WordPress Sites from Exploitation
SecureWorld News
FEBRUARY 19, 2024
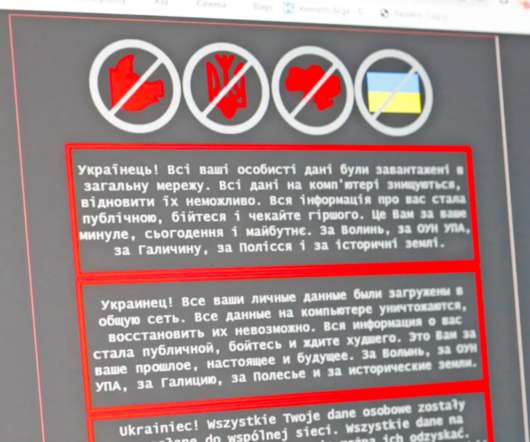
Hundreds of millions of websites on the internet today rely on the content management system WordPress. WordPress sites can be structured in an almost infinite number of ways, integrating with numerous other open-source plugins and third-party systems.











































Let's personalize your content