Life in 2050: How Will AI Shape the Future?
Information Week
SEPTEMBER 2, 2022
While artificial intelligence is already changing our world, it’s really only just begun. Here’s my vision of what life might be like in 2050.

Information Week
SEPTEMBER 2, 2022
While artificial intelligence is already changing our world, it’s really only just begun. Here’s my vision of what life might be like in 2050.

IT Toolbox
SEPTEMBER 30, 2022
AI-powered image generators create new challenges for visual artists to surmount. The post AI-powered Image Tools Create An Existential Crisis for Visual Artists appeared first on Spiceworks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Association of Information Technology Professional
SEPTEMBER 16, 2022
Ever wondered what are the best ethical certifications and how can they boost your career? Read along to find out what we recommend.

Tech Republic Cloud
SEPTEMBER 20, 2022
NVIDIA’s Omniverse Cloud platform aims to advance metaverse applications, robotics development, electric cars and biomedical discovery. The post NVIDIA unleashes Omniverse Cloud for industrial metaverse applications appeared first on TechRepublic.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Tech Republic Security
SEPTEMBER 29, 2022
Enterprise software delivery company CloudBees has a new SaaS offering to discuss, and the firm's CEO gets philosophical. The post CloudBees CEO: Software delivery is now ‘release orchestration’ appeared first on TechRepublic.
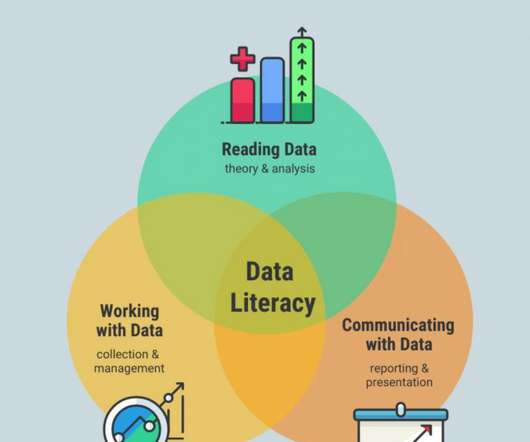
Tech Republic Data Center
SEPTEMBER 28, 2022
It doesn't matter what area you work in tech—even if you're only tech-adjacent—most organizations lag in efforts to ensure staff has the vital skill of a good grasp of data. The post Data literacy: Time to cure data phobia appeared first on TechRepublic.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

IT Toolbox
SEPTEMBER 30, 2022
Manual Testing is a time-consuming process. Here’s how automation can help streamline and boost the testing processes. The post To Code or Not to Code: The Benefits of Automating Software Testing appeared first on Spiceworks.

Anoop
SEPTEMBER 1, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows Autopatch Reports Stopped working after 29th August appeared first on HTMD Community Blog #1 Modern Device Management Guides by Admin.

Tech Republic Cloud
SEPTEMBER 3, 2022
See how 5G and 6G development are facing down their challenges to drive the future of tech toward innovation and industrial disruption. The post From 5G to 6G: The race for innovation and disruption appeared first on TechRepublic.

Tech Republic Security
SEPTEMBER 7, 2022
Learn more about how edge computing can reduce latency, boost performance and improve data security among other benefits. The post Benefits of edge computing appeared first on TechRepublic.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Network World
SEPTEMBER 14, 2022
A growing number of organizations are drawing an invisible line around their internet-connected resources in an effort to keep attackers at bay. Called software-defined perimeter (SDP), it is based on the relatively simple idea of throwing a virtual barrier around servers, routers, printers, and other enterprise network components. The goal of SDP is to protect networks behind a flexible, software-based perimeter.

Information Week
SEPTEMBER 16, 2022
The US government announced restrictions that limit Nvidia and Advanced Micro Devices AI chip sales to China. This regulatory move has a significant impact on the AI chip industry.

IT Toolbox
SEPTEMBER 8, 2022
Stateful tracks information about the state of a connection or application, while stateless does not. The post Stateful vs. Stateless: Understanding the Key Differences appeared first on Spiceworks.

Anoop
SEPTEMBER 30, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Detect Registry Changes and Revert using SCCM Configuration Item CI CB appeared first on HTMD Community Blog #1 Modern Device Management Guides by Abhinav Rana.

Advertiser: GEP
The technological landscape is dynamic and changes quickly. And for procurement and supply chain leaders looking to harness the power of technology to navigate complex challenges and an uncertain business environment, keeping up with the latest trends can be its own obstacle. So, what’s on the technological horizon for procurement and supply chain for the year ahead?

Tech Republic Cloud
SEPTEMBER 28, 2022
Cloud computing currently has a positive global market outlook, but some of its inadequacies may render it redundant in the future. The post Disadvantages of cloud computing appeared first on TechRepublic.

Tech Republic Security
SEPTEMBER 26, 2022
Jack Wallen details a recent hack and why he believes one aspect of two-factor authentication is part of the problem. The post Why 2FA is failing and what should be done about it appeared first on TechRepublic.
TechSpot
SEPTEMBER 16, 2022
A new agreement between the US Department of Commerce and Google could spark a surge of new chip designs and innovations. According to the DoC, the Google-NIST partnership answers one of the most pressing issues in the semiconductor industry: big corporations have ready access to new chips and designs, while.

Information Week
SEPTEMBER 20, 2022
From cybersecurity to metaverse, the COVID-19 pandemic has accelerated the adoption of digital technologies in almost every industry sector, and it is the impacting IT group.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

CIO Business Intelligence
SEPTEMBER 10, 2022
In the wake of the COVID-19 pandemic, airlines have struggled with bad weather, fewer air traffic controllers, and a shortage of pilots, all leading to an unprecedented number of cancelations in 2022. According to Reuters , more than 100,000 flights in the US were canceled between January and July, up 11% from pre-pandemic levels. American Airlines, the world’s largest airline, is turning to data and analytics to minimize disruptions and streamline operations with the aim of giving travelers a s

Anoop
SEPTEMBER 6, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows Autopilot Deployment Report appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Tech Republic Cloud
SEPTEMBER 26, 2022
Saad Mirza, Senior Director Solutions Architecture at Aviatrix, offers advice on how business can cope with a multicloud migration. The post Key considerations for enterprises moving to multicloud appeared first on TechRepublic.

Tech Republic Security
SEPTEMBER 28, 2022
Microsoft investigated a new kind of attack where malicious OAuth applications were deployed on compromised cloud tenants before being used for mass spamming. The post Malicious Oauth app enables attackers to send spam through corporate cloud tenants appeared first on TechRepublic.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.
TechSpot
SEPTEMBER 6, 2022
Peter Eckersley is not one of the most well-known names in the computer industry, but his contribution to modern internet and technology are notable. A computer scientist born in Melbourne, Australia, Eckersley worked at the Electronic Frontier Foundation and elsewhere to improve and advocate privacy, net neutrality and online security.

Information Week
SEPTEMBER 23, 2022
Here’s a curated collection of our articles on what the banking and investment sectors are doing with new financial technologies and how those techs prepare businesses for the future.

CIO Business Intelligence
SEPTEMBER 23, 2022
Employee experience has become a key factor in defining your company’s overall success. Positive or negative, employee experience can significantly impact your company’s productivity, efficiency, and its ability to recruit and retain talent. It can even impact your brand’s reputation long after an employee has exited the company. The COVID-19 pandemic has drastically changed the future of work by normalizing remote work , placing a new emphasis on workplace flexibility , and introducing hybrid w

Anoop
SEPTEMBER 22, 2022
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows 11 22H2 Group Policy Settings list Download appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Tech Republic Cloud
SEPTEMBER 28, 2022
Check out the pros and cons of multicloud and hybrid cloud deployment models, and get advice on what to consider when weighing your options. The post Multicloud vs hybrid cloud: Which one is right for your organization? appeared first on TechRepublic.

Tech Republic Security
SEPTEMBER 30, 2022
A new malware named Chaos raises concerns as it spreads on multiple architectures and operating systems. The post New Chaos malware spreads over multiple architectures appeared first on TechRepublic.

TechSpot
SEPTEMBER 30, 2022
Zeroes and ones were promised to be the future, a digital media has taken over, but in some situations customers are returning to analog experiences in search of something more tangible.

Information Week
SEPTEMBER 8, 2022
Banks and financial institutions are turning to data analytics and AI to help Gen Z with planning and tapping into biometrics to assuage their cybersecurity concerns.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
Let's personalize your content