Migrating to VoIP
Spearline Testing
JANUARY 14, 2021
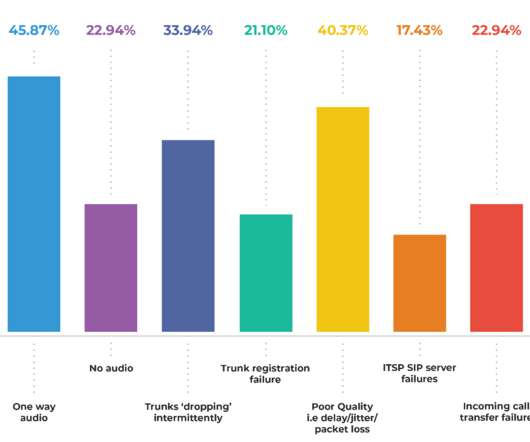
The growth of VoIP and SIP. Global Market Insights suggests that by 2025 the VoIP (Voice over Internet Protocol) market will have grown to $55 billion from approximately $20 billion in 2018. Secondly, rapid advancements in the overall telecommunications space and finally, the rise of remote working has been a key driver for VoIP.


















Let's personalize your content