Web 2.0 is Collapsing Under its Own Weight
Phil Windley
APRIL 4, 2024
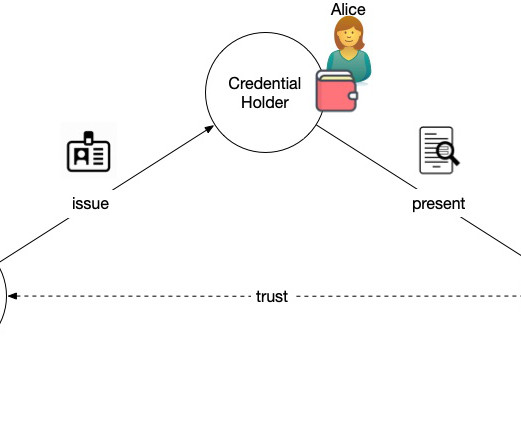
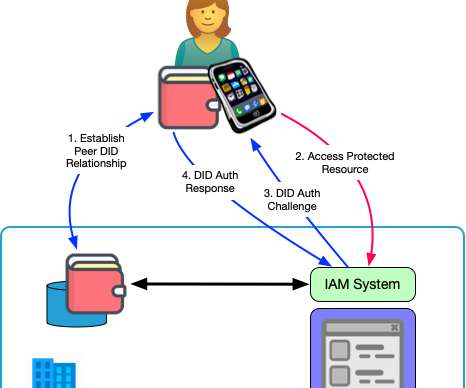
I think digital wallets (a bad name for an important tool), autonomic (peer) identifiers with strong cryptography, and verifiable credentials are a huge step forward. And part of that is being forced to use their inconvenient and anemic messaging systems. What's the answer? People need tools.

























Let's personalize your content