What Is an Evil Twin Attack? Definition, Detection, and Prevention Best Practices
IT Toolbox
MARCH 25, 2024
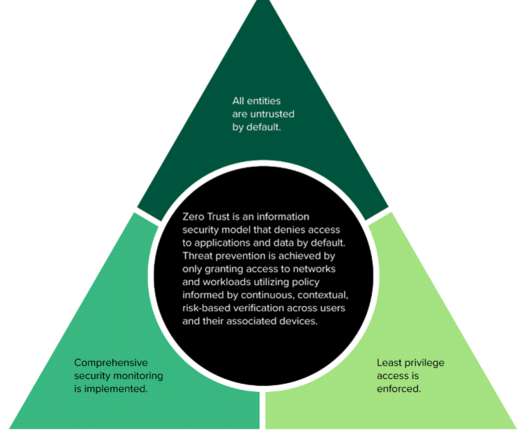
However, this dependence also exposes us to security vulnerabilities. Definition, Detection, and Prevention Best Practices appeared first on Spiceworks. One such threat is the deceptive evil twin attack. Read on to learn more. The post What Is an Evil Twin Attack?



















































Let's personalize your content