How DevOps Teams Get Automation Backwards
Information Week
NOVEMBER 16, 2020
Will automation speed up your processes, or will you end up with a brittle system that will demand constant attention and frequent, time-consuming fixes?

Information Week
NOVEMBER 16, 2020
Will automation speed up your processes, or will you end up with a brittle system that will demand constant attention and frequent, time-consuming fixes?
Forrester IT
NOVEMBER 18, 2020
It’s not that I’m not a gamer. I enjoy board games and card games: Trivial Pursuit, Settlers Of Catan, SET, Hive. I’m up to level 3056 in Two Dots. As a kid, I played Super Mario Land on my brother’s GameBoy and Sonic The Hedgehog on the family Sega Genesis. But I’ve never been one […].
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CTOvision
NOVEMBER 18, 2020
Bring Your Own Device (BYOD) used to be an emerging trend in the workplace, one that allowed professionals a bit more flexibility and comfort by using their personal computers and […].

Association of Information Technology Professional
NOVEMBER 19, 2020
CompTIA’s IT Industry Outlook 2021, with the theme “Rebuilding for the Future,” provides 10 trends in technology for the year ahead. For those in the business of technology, here are four ways to leverage the insights from CompTIA's latest research.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Tech Republic Security
NOVEMBER 20, 2020
IBM, Honeywell, and Intel are just three companies leading the way in building quantum machines as well as the algorithms and controls to run them. Learn about possible business use cases for quantum.

Forrester IT
NOVEMBER 20, 2020
One of the best parts of being a Forrester analyst is having the time, space, and data to wrestle with abstract, complex concepts that inevitably influence business today and in the near future. For the past several months, I’ve been chipping away at a topic that is on the minds of leaders in just about […].
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Association of Information Technology Professional
NOVEMBER 18, 2020
Learn about the cybersecurity industry for beginners and how you can further your cybersecurity career with IT certifications like CompTIA Security+.

Information Week
NOVEMBER 17, 2020
Across industries, big data has joined traditional, structured data as a mission-critical element. Here's some advice for CIOs and big data leaders on how to get started.

Tech Republic Security
NOVEMBER 16, 2020
Implementing appropriate data privacy is critical for company operations and success. Learn some of the challenges and solutions recommended to do the job right.

Anoop
NOVEMBER 19, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. In this post, we learn about ConfigMgr Task Sequence OSD Multiple Physical Drives. Let’s try to understand how can we use conditions in the Task sequence to install operating systems via SCCM Task Sequence on a machine having dual drives. The below articles will give you an idea about the scenario which I have faced […].

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Association of Information Technology Professional
NOVEMBER 18, 2020
CompTIA PenTest+ is now approved by the U.S. Department of Defense (DoD) 8570 for three cybersecurity job categories.

All Things Distributed
NOVEMBER 19, 2020
Growing up in the Netherlands, American football was largely a foreign concept to me. My version of football was The Beautiful Game , or as most Americans know it, soccer. Football, futbol, soccer, or whatever else you call it, will always be something I’m deeply passionate about, especially my hometown team, Ajax. When I joined Amazon and Seattle became my new home, I began to see how my colleagues shared this same level of passion for American football – and particularly the fervent fans known

Tech Republic Security
NOVEMBER 18, 2020
This year was rough for all involved--even Linux and open source didn't come through unscathed. See what Jack Wallen considers to be the biggest issue for Linux in 2020.

Anoop
NOVEMBER 17, 2020
Subscribe YouTube Channel [link]. and Facebook Page to get latest updates. [link]. Today’s blog post focuses on the Support Assist feature of Admin By Request. What is Admin By Request? Admin By Request from Fastrack Software is a Privileged Access Management (PAM) solution for Windows (Server/Client) and Mac endpoints that allows you to revoke local admin rights of the end-users from the workstations/endpoints without interrupting normal work flows.

Advertiser: GEP
The technological landscape is dynamic and changes quickly. And for procurement and supply chain leaders looking to harness the power of technology to navigate complex challenges and an uncertain business environment, keeping up with the latest trends can be its own obstacle. So, what’s on the technological horizon for procurement and supply chain for the year ahead?

Association of Information Technology Professional
NOVEMBER 16, 2020
A recent CompTIA research study revealed the cybersecurity skills IT pros need to build their knowledge base and careers.

Tech Republic Cloud
NOVEMBER 16, 2020
COVID-19 sent cloud adoption into overdrive; its role in digital transformation is uncontested, but just 37% of companies say they've realized the full potential of investments, according to Accenture.

Network World
NOVEMBER 16, 2020
In its second cloud-native technology acquisition in as many months, Cisco is buying container security firm Banzai Cloud for an undisclosed amount. Founded in 2017, Banzai is known for developing Kubernetes-based cloud application development and security technologies. It will become part of Cisco's Emerging Technologies and Incubation group, where the company brews new projects for cloud-native networking, security and edge computing environments.

Information Week
NOVEMBER 18, 2020
CIOs will have a host of cloud options to choose from in 2021 as the cloud business evolves, according to a new Forrester Research report.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.
Tech Republic Security
NOVEMBER 19, 2020
Cybercriminals are taking advantage of Google's open and accessible online tools to skirt past the usual security filters, says Armorblox.

Tech Republic Cloud
NOVEMBER 17, 2020
Most organizations plan to increase their cloud spending in the midst of the side effects of the coronavirus pandemic, says Gartner.

The Verge
NOVEMBER 20, 2020
Photo by Deborah Feingold/Getty Images. From Windows 1.0 to Windows 10 The PC revolution started off life 35 years ago this week. Microsoft launched its first version of Windows on November 20th, 1985, to succeed MS-DOS. It was a huge milestone that paved the way for the modern versions of Windows we use today. While Windows 10 doesn’t look anything like Windows 1.0, it still has many of its original fundamentals like scroll bars, drop-down menus, icons, dialog boxes, and apps like Notepad and M

Information Week
NOVEMBER 20, 2020
Focus on the marathon, not the sprint. Here are three best practices for constructing effective, efficient dev teams.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.
Tech Republic Security
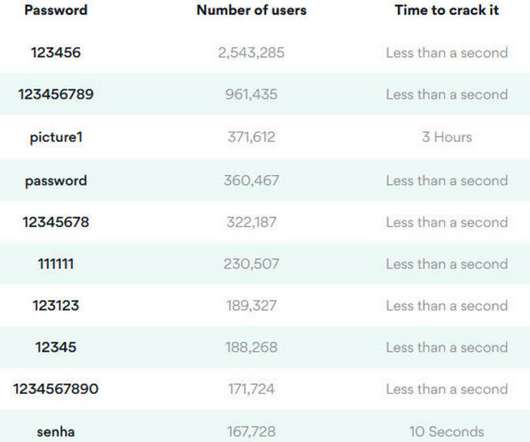
NOVEMBER 18, 2020
People are still using very simple passwords, with many of them similar to the ones they used in 2019, according to NordPass.

Tech Republic Cloud
NOVEMBER 20, 2020
You can now use Teams to call friends and family free of charge, even if they don't have the app installed.

The Verge
NOVEMBER 20, 2020
Illustration by Alex Castro / The Verge. T-Mobile has added support for the 988 emergency mental health services number more than a year and a half ahead of the Federal Communications Commission’s deadline, the company announced on Friday. T-Mobile customers who dial 988 will be connected to the National Suicide Prevention Lifeline (NSPL) and its network of crisis centers across the US.

Gizmodo
NOVEMBER 19, 2020
This week, the Rockefeller Center Christmas tree was unfurled in all its floppy, haggard glory. As many a Twitter user were quick to point out, its appearance was a metaphor for this year of pandemic, a slapdash coup attempt, and a general drubbing of American exceptionalism. Read more.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
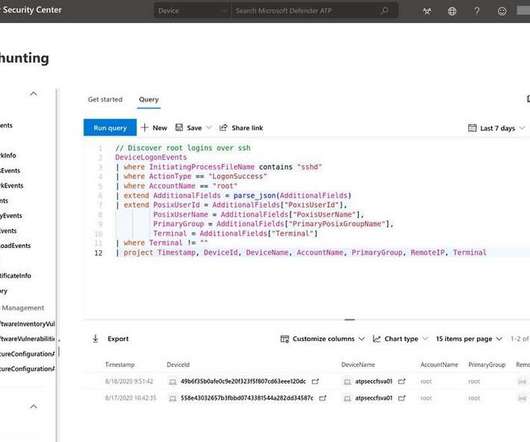
Tech Republic Security
NOVEMBER 19, 2020
Linux endpoint detection and response will help Microsoft Defender customers secure Linux servers and networks against security nasties.

GeekWire
NOVEMBER 19, 2020
Sunset over the Seattle skyline. (GeekWire Photo / Kevin Lisota). Enterprise software companies have long dominated the Seattle and Pacific Northwest tech scene. They range from stalwarts such as Microsoft and F5 Networks, to a bevy of smaller startups developing cutting-edge software in cloud computing, cybersecurity, and other industries. As the COVID-19 pandemic accelerates adoption of digital technology , the spotlight is shining brighter on the robust business-to-business technology ecosyst

The Verge
NOVEMBER 20, 2020
Photo by Vjeran Pavic / The Verge. Last week I wrote that Apple seemed “astonishingly confident” in its new M1-based Macs. This week we know why: they are astonishingly good. I reviewed the MacBook Air , Nilay Patel reviewed the entry-level 13-inch MacBook Pro , and Chris Welch reviewed the new Mac mini. All three are equally impressive, but it’s the Air in particular that stands out as offering incredible power at its price point.

Gizmodo
NOVEMBER 19, 2020
The recent failure of two support cables at the Arecibo Observatory in Puerto Rico has destabilized the structure such that it cannot be repaired without placing construction workers at significant risk, according to officials with the National Science Foundation. As feared, the beloved 1,000-foot telescope will have… Read more.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.
Let's personalize your content