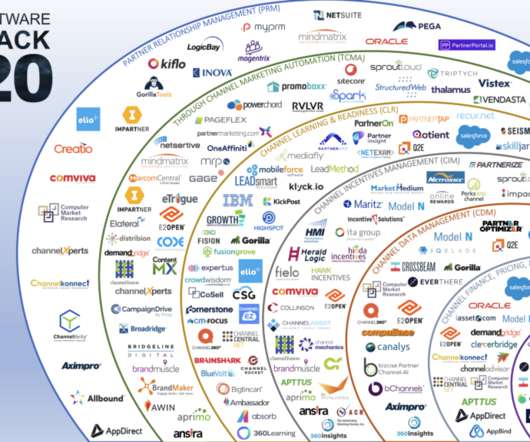
Channel Software Tech Stack 2020 – PRM, TCMA, Ecosystem, Incentives, Channel Data, Learning, Readiness, and Pricing
Forrester IT
JUNE 26, 2020
^^ CLICK IMAGE FOR FULL SCREEN ^^ The channel technology stack is a group of technologies that firms leverage to plan with, find, recruit, onboard, develop, enable, incentivize, co-sell with, co-market with, manage, measure, and report on partners. Delivering automation of indirect sales processes, workflows and partner programs, channel software is becoming increasingly critical […].









































Let's personalize your content