What current service operation investment says about CSPs’ strategies
TM Forum
MAY 26, 2022
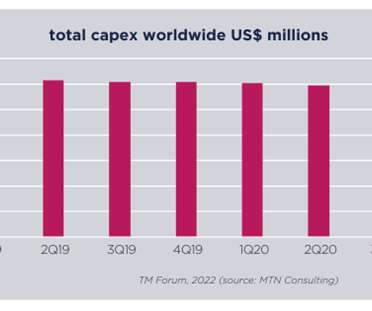
At the same time, these current hotspots of OSS/BSS spending tally with a shift away from network-heavy and towards a renewed focus on IT systems (and related vendor professional services). There is also something else going on here, and it relates to both the near future and the longer term ecosystem.
























Let's personalize your content