Report: Attackers Move Lightning Fast to Capitalize on Vulnerabilities
SecureWorld News
DECEMBER 18, 2023
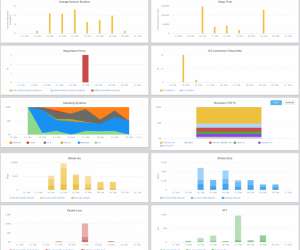
Its analysis reveals a startling insight into how quickly attackers capitalize on these vulnerabilities. This immediate action represents a shift in the modus operandi of attackers, highlighting their growing efficiency and the ever-decreasing window for response by defenders. 115 exploited by named threat actors.














































Let's personalize your content