In A Multi-Cloud World, Web Application Firewalls Still Matter
Forrester IT
MAY 2, 2022
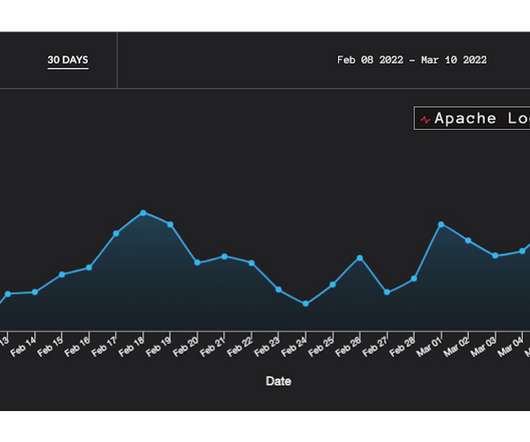
If you hadn’t thought about web application firewalls (WAFs) in a while, you might think they were an anachronism, a tool of the past that modern application environments don’t bother with. You’d be wrong.

















































Let's personalize your content