ANY.RUN vs. Joe Sandbox: Malware analysis tools comparison
Tech Republic
MARCH 23, 2022
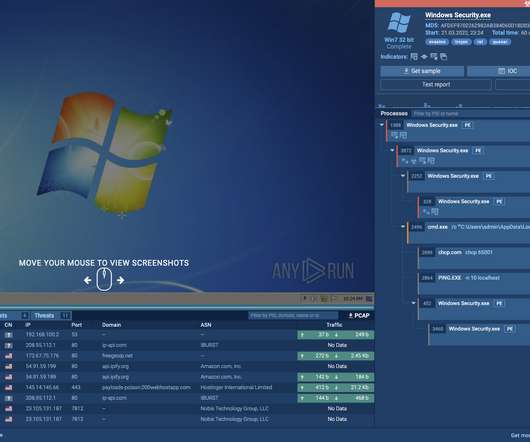
Malware analysis sandboxes let users determine if a file or URL is malicious, suspicious or legitimate. The post ANY.RUN vs. Joe Sandbox: Malware analysis tools comparison appeared first on TechRepublic. For daily use, two good solutions are ANY.RUN and Joe Sandbox. Let’s compare their features.



























Let's personalize your content