What Is Authentication? Meaning, Types, and Tools
IT Toolbox
DECEMBER 4, 2023
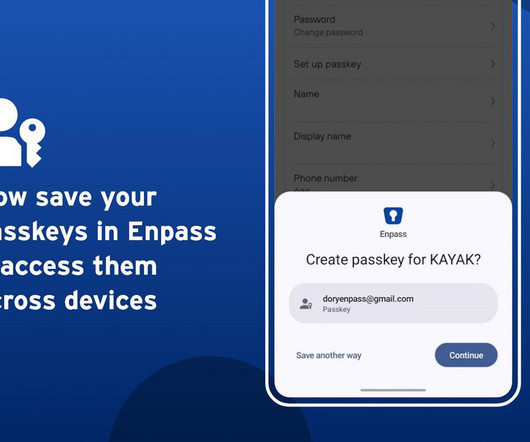
Authentication allows the verification of user identity, ensuring only authorized access to systems, services, and resources. The post What Is Authentication? Meaning, Types, and Tools appeared first on Spiceworks.



















































Let's personalize your content