4 Best Open Source Password Managers for Teams in 2024
Tech Republic Security
APRIL 11, 2024
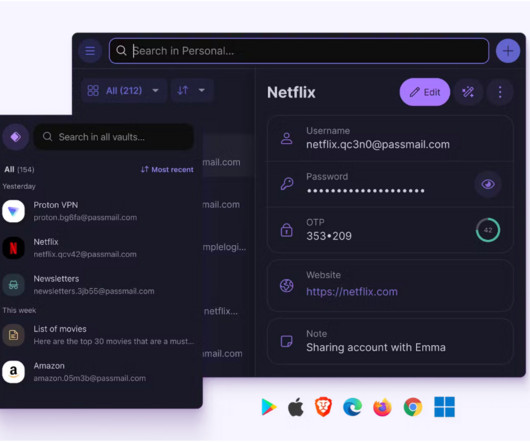
Find the best open-source password managers to keep your sensitive information secure and easily accessible. Explore top options for protecting your passwords.














































Let's personalize your content