Microsoft targets CAPTCHA-cracking bot ring allegedly responsible for 750M fake accounts
GeekWire
DECEMBER 13, 2023
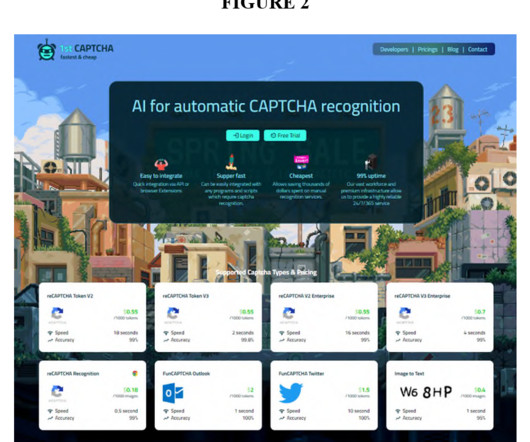
As shown in court documents, this is the 1stCAPTCHA site where Microsoft says the defendants sold CAPTCHA-solving tokens obtained by a fleet of bots. This is one of the domains siezed by the company via court order. Screenshot via U.S. District Court for the Southern District of New York.) District Court for the Southern District of New York.











































Let's personalize your content