What Is SD-WAN (Software-Defined WAN)? Definition, Solutions, and Benefits
IT Toolbox
SEPTEMBER 1, 2022
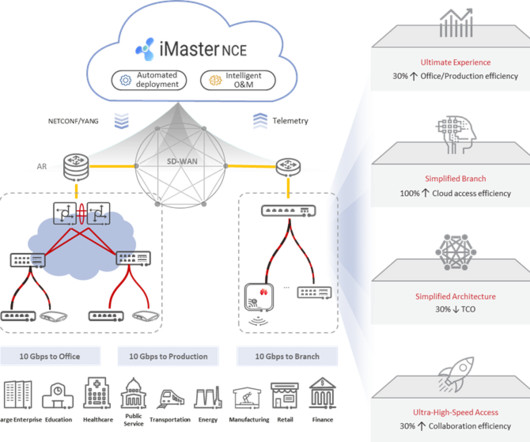
Increasingly used in large network setups, SD-WAN uses web-based tunnels, firewall software, and virtual technologies to connect remote endpoints. Definition, Solutions, and Benefits appeared first on Spiceworks. The post What Is SD-WAN (Software-Defined WAN)?












































Let's personalize your content