AI focus shifts to ‘small and wide’ data
Venture Beast
SEPTEMBER 7, 2021
A Gartner report finds that companies will increasingly embrace responsible AI while seeking ways to more efficiently deploy AI systems. Read More.

Venture Beast
SEPTEMBER 7, 2021
A Gartner report finds that companies will increasingly embrace responsible AI while seeking ways to more efficiently deploy AI systems. Read More.

Social, Agile and Transformation
SEPTEMBER 7, 2021
Labor Day has new meaning in our house. I have tremendous new respect for all people who earn their living from hard, sweaty, dirty work. And yet, while I call this my personal disaster recovery, it really isn't that personal or that significant of a disaster. My family and I came home to Hurricane Ida's wreckage after it dumped an estimated seven inches of rain in our town.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Association of Information Technology Professional
SEPTEMBER 8, 2021
Learn how pen testing and vulnerability assessment work together to strengthen a cybersecurity strategy, and how CompTIA PenTest+ can teach you these skills.

Tech Republic Security
SEPTEMBER 9, 2021
Some of these phrasings are standard day-to-day subject lines, but as one expert explained, "the attacker wants you to be moving too fast to stop and question if it's legitimate.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Anoop
SEPTEMBER 10, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Intune Security Baseline Microsoft Defender Policy Troubleshooting Tips for Cloud PCs appeared first on HTMD Blog #1 by Anoop C Nair.

Information Week
SEPTEMBER 10, 2021
Business/citizen developers will neither take over the world nor ruin it. Rather than focus on extremes, enterprises should consider the targeted use cases for low code.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
SEPTEMBER 9, 2021
IT teams are experiencing employee pushback due to remote work policies and many feel like cybersecurity is a "thankless task" and that they're the "bad guys" for implementing these rules.

Anoop
SEPTEMBER 8, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Enable Windows 11 Patching using SCCM WSUS appeared first on HTMD Blog #1 by Anoop C Nair.

All Things Distributed
SEPTEMBER 7, 2021
In the age of cloud, problem-solving has evolved, especially when it comes to the world's hardest problems.

Tech Republic Cloud
SEPTEMBER 10, 2021
Choosing CRM software is difficult with all of the options available. Compare features of the best CRM tools of 2021.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Tech Republic Security
SEPTEMBER 8, 2021
Technology is not the only answer: An expert suggests improving the human cyber capacity of a company's workforce plus cybersecurity technology offers a better chance of being safe.

Anoop
SEPTEMBER 6, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Download Intune CIS Benchmark for Windows 10 appeared first on HTMD Blog #1 by Anoop C Nair.

Information Week
SEPTEMBER 8, 2021
If optimizing your cloud spending is on your to-do list this year, these tips could help you stay within budget.
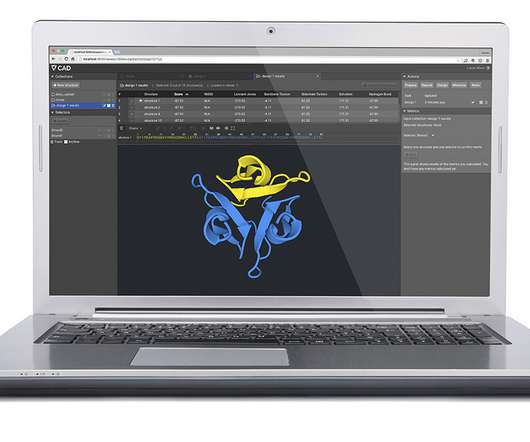
GeekWire
SEPTEMBER 9, 2021
Cyrus Biotechnology has several drug discovery and development partnerships and also sells Cyrus Bench, a software platform for protein engineering. (Cyrus Photo). Seattle-based Cyrus Biotechnology is entering a protein engineering collaboration with Boston-based Selecta Biosciences that could pull in up to $1.5 billion for the University of Washington spinout.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Tech Republic Security
SEPTEMBER 9, 2021
Cyberattacks have surged during the coronavirus pandemic as criminals rake in bountiful ransomware payouts. Malicious office docs have been on the rise for months, per a new report.

Anoop
SEPTEMBER 8, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Cloud PC Monthly Patching Process using Intune appeared first on HTMD Blog #1 by Anoop C Nair.

Gizmodo
SEPTEMBER 8, 2021
The world’s biggest direct air capture (DAC) plant is set to come online in Iceland on Wednesday. The moment is an important one in developing new technologies to help suck carbon dioxide out of the air —but raises a whole host of questions on the future of how we’re going to put those technologies to use. Read more.

GeekWire
SEPTEMBER 9, 2021
Microsoft CEO Satya Nadella and LinkedIn CEO Ryan Roslansky discuss workplace trends in a webcast released Thursday morning , highlighting new research and product features from the company for remote and hybrid work. A new study finds that Microsoft’s companywide shift to remote work has hurt communication and collaboration among different business groups inside the company, threatening employee productivity and long-term innovation.

Advertisement
You’ve read the PMBOK® Guide several times, taken the certification exam for project managers, passed, and you are now a PMP®. So why do you keep making rookie mistakes? This whitepaper shows 20 of the most common mistakes that young or inexperienced project managers make, issues that can cost significant time and money. It's a good starting point for understanding how and why many PMs get themsleves into trouble, and provides guidance on the types of issues that PMs need to understand.

Tech Republic Security
SEPTEMBER 8, 2021
Only 33% of users surveyed by NordPass changed the default passwords on their IoT devices, leaving the rest susceptible to attack.

Anoop
SEPTEMBER 6, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Outlook Web App OWA instead of Outlook Desktop App 4 Months Experience appeared first on HTMD Blog #1 by Anoop C Nair.
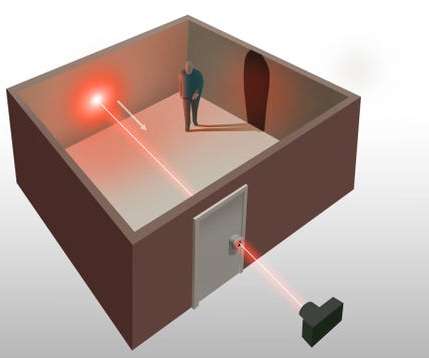
Gizmodo
SEPTEMBER 8, 2021
Being able to see inside a closed room was a skill once reserved for super heroes. But researchers at the Stanford Computational Imaging Lab have expanded on a technique called non-line-of-sight imaging so that just a single point of laser light entering a room can be used to see what physical objects might be inside. Read more.

TechSpot
SEPTEMBER 7, 2021
Anti-Cheat Police Department, a Twitter account that aggregates reports on cheating in online games, recently collected some forum posts from users having issues running Valorant on Windows 11. They show a "VAN9001" error that seems to occur when trying to play Valorant on Windows 11 without TPM2.0 or secure boot.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Tech Republic Security
SEPTEMBER 8, 2021
Making predictions about data is the next frontier in terms of identifying risk in your infrastructure, expert says. But is it right for your organization?

Anoop
SEPTEMBER 9, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post Windows 11 with Recycle Bin Modern Context Menu Adoption Preview Build appeared first on HTMD Blog #1 by Anoop C Nair.

GeekWire
SEPTEMBER 10, 2021
An artist’s conception shows BlackSky’s Global satellites in orbit. (BlackSky Illustration). BlackSky , the geospatial data analysis company that got its start in Seattle, eased into its first day of public trading on the New York Stock Exchange today, clinching a blank-check merger deal that unlocked about $283 million in capital. The business combination with Osprey Technology Acquisition Corp. — a special-purpose acquisition company, or SPAC — was approved by Osprey’s shareh

The Verge
SEPTEMBER 7, 2021
A promo image for Apple’s next event. | Image: Apple. Apple’s next big fall event will take place on Tuesday, September 14th at 1PM ET, the company announced. The event, which carries the tagline “California streaming,” will be another virtual event broadcast from Apple Park. The company typically announces the year’s new iPhones at the fall event, and this year’s entry is expected to be called the iPhone 13.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Tech Republic Security
SEPTEMBER 9, 2021
Chances are good you're not using your browser with a strong enough eye on security. Jack Wallen offers up some advice to the average user on how to browse safer.

Anoop
SEPTEMBER 8, 2021
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link]. and Facebook Page to get the latest updates. [link]. Read More. The post SCCM to Fix New Remote Code Execution Vulnerability in MSHTML component appeared first on HTMD Blog #1 by Anoop C Nair.

GeekWire
SEPTEMBER 7, 2021
Pro.com CEO Matt Williams. (Pro.com Photo). Opendoor , the online real estate giant that lets people directly buy and sell homes online, has acquired Seattle-based startup Pro.com and San Francisco-based Skylight. Terms of the deals were not disclosed. Both platforms, which offered digital home improvement services, will be discontinued. “The additions of the Skylight and Pro.com teams will bring on like-minded founders and teammates who care deeply about transforming housing,” Opend

The Verge
SEPTEMBER 6, 2021
Illustration by Alex Castro / The Verge. Automated resume-scanning software is contributing to a “broken” hiring system in the US, says a new report from Harvard Business School. Such software is used by employers to filter job applicants, but is mistakenly rejecting millions of viable candidates, say the study’s authors. It’s contributing to the problem of “hidden workers” — individuals who are able and willing to work, but remain locked out of jobs by structural problems in the labor market.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Let's personalize your content