What is Nmap and why do you need it on your network?
Network World
MAY 19, 2022
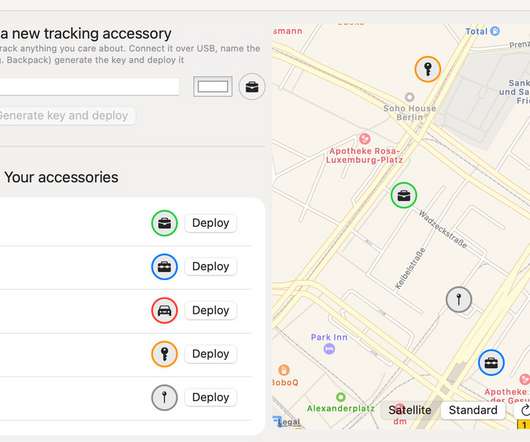
Nmap, short for Network Mapper, is a free and open source tool used for vulnerability checking, port scanning and, of course, network mapping. Despite being created back in 1997, Nmap remains the gold standard against which all other similar tools , either commercial or open source, are judged.













































Let's personalize your content