What Is a DISA Security Technical Implementation Guide (STIG)? Definition, Application, and Compliance Levels
IT Toolbox
FEBRUARY 23, 2024
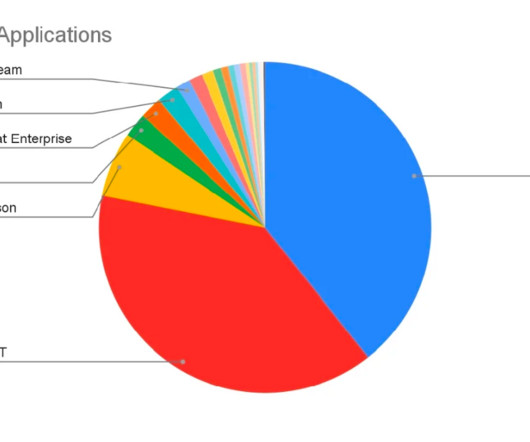
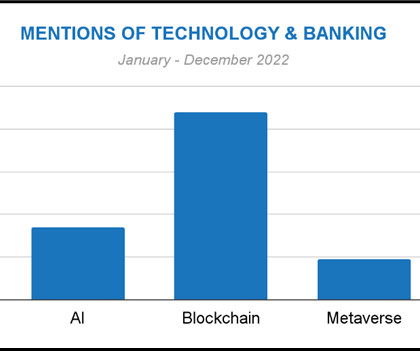
Security Technical Implementation Guides (STIGs) are detailed, prescriptive documents outlining standardized security configurations for specific platforms, software, and network devices. The post What Is a DISA Security Technical Implementation Guide (STIG)? Learn more about these guides.














































Let's personalize your content