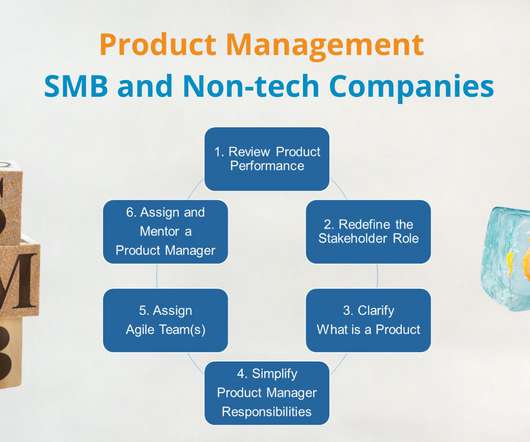
How to Innovate by Introducing Product Management in SMB and Non-Tech Companies
Social, Agile and Transformation
DECEMBER 12, 2022
I learned two truths this week. During the Coffee with Digital Trailblazers, a LinkedIn audio event that I host most Fridays at 11 am ET, Jay Cohen shared that January was a good time of the year to focus on learning programs and driving department and team-level realignments. It makes sense because people return to work from the holidays refreshed and ready to learn.










































Let's personalize your content