Why a College Degree is No Longer Necessary for IT Success
Information Week
MARCH 29, 2023
Who needs student debt? A growing number of employers are hiring IT pros with little or no college experience.

Information Week
MARCH 29, 2023
Who needs student debt? A growing number of employers are hiring IT pros with little or no college experience.

Tech Republic Security
MARCH 15, 2023
AI-generated phishing emails, including ones created by ChatGPT, present a potential new threat for security professionals, says Hoxhunt. The post Humans are still better at creating phishing emails than AI — for now appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Toolbox
MARCH 27, 2023
What does ChatGPT have in store for active directory (AD) security? The post ChatGPT: A Blessing or a Curse for AD Security? appeared first on Spiceworks.

Social, Agile and Transformation
MARCH 20, 2023
I’ve led many successful application development, cloud migration, and data/analytics programs over the years, and I staffed most of them with a mix of employees, freelancers, and service providers.

Advertisement
With its unparalleled flexibility, rapid development and cost-saving capabilities, open source is proving time and again that it’s the leader in data management. But as the growth in open source adoption increases, so does the complexity of your data infrastructure. In this Analyst Brief developed with IDC, discover how and why the best solution to this complexity is a managed service, including: Streamlined compliance with some of the most complex regulatory guidelines Simplified operations, li
Anoop
MARCH 30, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Intune Advanced App and Vulnerability Management for 3rd Party Patch Management from Microsoft appeared first on HTMD Community Blog #1 Modern Device Management Guides by Vidya M A.
Tech Republic Cloud
MARCH 17, 2023
Google jostles with AI rivals as it releases a large language model API and other developer tools. The post Google Cloud opens enterprise AI tools to developers appeared first on TechRepublic.
Information Technology Zone brings together the best content for IT professionals from the widest variety of industry thought leaders.

Tech Republic Security
MARCH 29, 2023
Learn how to protect your organization and users from this Android banking trojan. The post Nexus Android malware targets 450 financial applications appeared first on TechRepublic.

IT Toolbox
MARCH 27, 2023
Aberdeen Strategy & Research narrowed down three key steps to ensure companies drive operational efficiency and improve their competitive positioning by using AI in CX. The post Three Building Blocks of AI-Driven Success in CX appeared first on Spiceworks.

TechSpot
MARCH 30, 2023
An official reading mode for the Chrome desktop browser and ChromeOS was one of several education-focused features Google previewed at BETT 2023. Rather than stripping a page down to its basic text to make it easier to read, Chrome's take is in the form of a customizable sidebar that replicates.
Anoop
MARCH 14, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post FIX Zero Day Security Vulnerability for Outlook appeared first on HTMD Community Blog #1 Modern Device Management Guides by Anoop C Nair.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.

Tech Republic Cloud
MARCH 14, 2023
What’s driving the growth of open source container orchestrator Kubernetes? A study by Pepperdata shows how companies are using K8s and the challenges they face in getting a handle on cloud costs. The post Kubernetes is the key to cloud, but cost containment is critical appeared first on TechRepublic.

Information Week
MARCH 21, 2023
The growing focus and availability of generative AI, such as ChatGPT, present new challenges to cybersecurity teams, foreshadowing an era of machine versus machine threats and defenses.

Tech Republic Security
MARCH 30, 2023
The new AI security tool, which can answer questions about vulnerabilities and reverse-engineer problems, is now in preview. The post Microsoft adds GPT-4 to its defensive suite in Security Copilot appeared first on TechRepublic.

IT Toolbox
MARCH 22, 2023
Here are the benefits of incorporating AI into the HR and recruitment processes. The post Leveraging AI To Improve the Candidate Experience appeared first on Spiceworks.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.
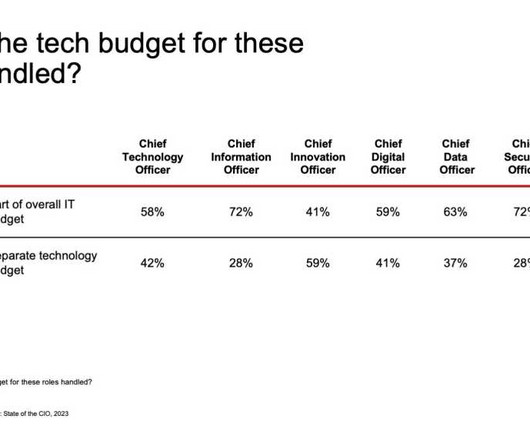
CIO Business Intelligence
MARCH 27, 2023
Chief data and analytics officers (CDAOs) are poised to be of increasing strategic importance to their organizations, but many are struggling to make headway, according to data presented last week by Gartner at the Gartner Data & Analytics Summit 2023. Fewer than half (44%) of data and analytics leaders say their teams are effective in providing value to their organization.

Anoop
MARCH 2, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post New Microsoft Intune Suite for Endpoint Management appeared first on HTMD Community Blog #1 Modern Device Management Guides by Jitesh Kumar.

Tech Republic Cloud
MARCH 8, 2023
Communications service providers will be able to operate and observe private 5G environments in a unified management stack. The post IBM and Nokia announce plans for a private 5G service appeared first on TechRepublic.

Information Week
MARCH 3, 2023
Ransomware shut down the produce company’s North American operations, leading to a salad shortage. Other critical infrastructure operations face the same kinds of attacks and an evolving threat landscape.

Advertiser: Procom Services
From streamlining the job search process to efficiently navigating the influx of applications, AI-powered tools can revolutionize your recruitment efforts. By combining the efficiency of AI with the expertise of experienced recruiters, you can identify the ideal candidates who not only possess the necessary skills but also align with your company culture.

Tech Republic Security
MARCH 23, 2023
Microsoft has already seen millions of phishing emails sent every day by attackers using this phishing kit. Learn how to protect your business from this AitM campaign. The post Massive adversary-in-the-middle phishing campaign bypasses MFA and mimics Microsoft Office appeared first on TechRepublic.

IT Toolbox
MARCH 1, 2023
Discover the ethical pitfalls that AI developers need to be aware of. The post How Can AI Developers Avoid Ethical Landmines? appeared first on Spiceworks.

TechSpot
MARCH 24, 2023
United Airlines, in collaboration with Archer Aviation, have unveiled their plan to start an air taxi service in Chicago in 2025. The aircraft made by Archer is named Midnight and is designed to fly up to 100 miles, but is optimized for short flights of roughly 20 miles, according to the company.

Anoop
MARCH 7, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Enroll iOS/iPadOS Devices in Intune Step by Step Guide appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren.

Speaker: Kat Conner
The challenge of delivering the right product at the right time while aligning with strategic objectives is more pressing than ever. Product management is evolving and gaining greater recognition as the means to creating this connection. Join our upcoming webinar and learn how to streamline your product development processes, infuse product thinking across the organization, and bridge the gap between vision and delivery.

GeekWire
MARCH 25, 2023
Seattle-based Game to Grow released its simple, therapeutic tabletop game Critical Core in October. (Game to Grow Image) A new whitepaper from two Seattle organizations exhibits research into how tabletop roleplaying games, such as Wizards of the Coast’s Dungeons & Dragons , can be used to help children and teenagers develop their social skills.

Information Week
MARCH 16, 2023
Cyber criminals are likely to exploit the power of generative AI platforms -- including ChatGPT -- to make phishing attacks or other malicious activity more difficult to stop.

Tech Republic Security
MARCH 30, 2023
New studies by NCC Group and Barracuda Networks show threat actors are increasing ransomware exploits, with consumer goods and services receiving the brunt of attacks and a large percentage of victims being hit multiple times. The post Ransomware attacks skyrocket as threat actors double down on U.S., global attacks appeared first on TechRepublic.
IT Toolbox
MARCH 29, 2023
Learn how content marketers can leverage AI for content creation. The post 4 Ways AI Is Changing Content Creation and Marketing as We Know It appeared first on Spiceworks.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr

TechSpot
MARCH 27, 2023
Nammo, an ammo manufacturer co-owned by the Norwegian government and a Finnish state-controlled defense company, cannot meet the increasing demand for its artillery rounds because a local data center, whose primary customer is TikTok, is using all the electricity in the region, preventing a planned expansion of Nammo's factory.

Anoop
MARCH 2, 2023
Hello - Here is the new HTMD Blog Article for you. Enjoy reading it. Subscribe to YouTube Channel [link] and Facebook Page to get the latest updates [link]. Read More The post Create Intune Compliance Policy for iOS iPadOS Devices appeared first on HTMD Community Blog #1 Modern Device Management Guides by Malepati Naren.

CIO Business Intelligence
MARCH 13, 2023
Diversity is critical to IT performance. Diverse teams perform better, hire better talent, have more engaged members, and retain workers better than those that do not focus on diversity and inclusion, according to a 2020 report from McKinsey. Despite this, women remain widely underrepresented in IT roles. And the numbers back up this assertion, often in stark ways.

Information Week
MARCH 1, 2023
If you’re an IT leader or tech manager struggling to hire for one of these positions, you’re not alone. If you’re an IT professional with experience in these roles, you’re in luck.

Advertisement
It’s no surprise that Apache Cassandra has emerged as a popular choice for organizations of all sizes seeking a powerful solution to manage their data at a scale—but with great power comes great responsibility. Due to the inherent complexity of distributed databases, this white paper will uncover the 10 rules you’ll want to know when managing Apache Cassandra.
Let's personalize your content